Blocking BlackCat with Cubic-Crystal System
By Beijing Mike
1. BlackCat/ALPHV ransomware
The BlackCat group is a sophisticated RaaS operation, active since November 2021, known for using a variety of methods to infiltrate victim networks, including exploiting known vulnerabilities, phishing attacks, and social engineering. Once inside a network, BlackCat operators typically use a combination of tools and techniques to move laterally, escalate privileges, and exfiltrate data. The group then deploys its ransomware payload, which encrypts the victim’s files.
BlackCat is implemented in the Rust programming language, which is efficient for file encryption and cross-platform compatibility. Files are encrypted using a per-file AES key encrypted using a per-victim RSA public key. Because BlackCat leverages an affiliate network to conduct breaches, exfiltrate data, and deploy the ransomware, the flow of attacks varies widely between affiliates. When victims pay a ransom for file decryption, they receive BlackCat decryption tools for 11 different platforms.
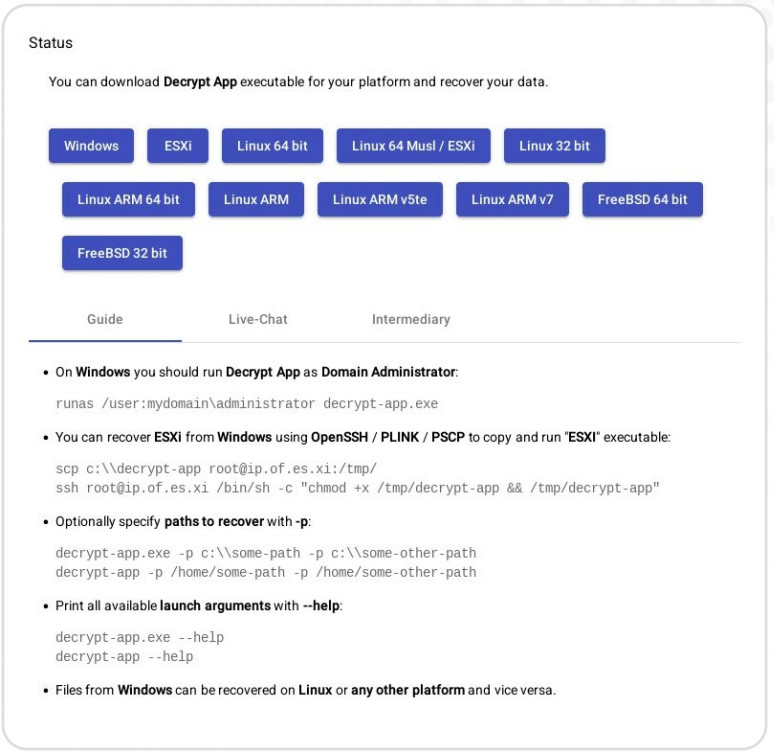
BlackCat/ALPHV decryption tools spanning 11 different platforms
2. BlackCat/ALPHV infection chain
The following example demonstrates an attack carried out by a BlackCat affiliate. The initial attack took advantage of vulnerabilities in Microsoft Exchange, namely CVE-2021-26855, CVE-2021- 26857, CVE-2021-26858, and CVE-2021-27065, which enabled the execution of remote code on the targeted server.
In the sample analyzed for this use case, the BlackCat affiliate exploited four vulnerabilities in Microsoft Exchange to gain initial access to the victim’s network. Once inside, the attackers used a variety of tools and techniques to gather information about the victim’s environment, including cmd.exe, net.exe, ADRecon, and AdFind. The attackers then extracted credentials from the lsass.exe process, which allowed them to move laterally using RDP.
Once they had access to the victim’s critical systems, the attackers used MegaSync and Rclone to exfiltrate data. Finally, the attackers used PsExec to remotely execute the BlackCat ransomware payload.
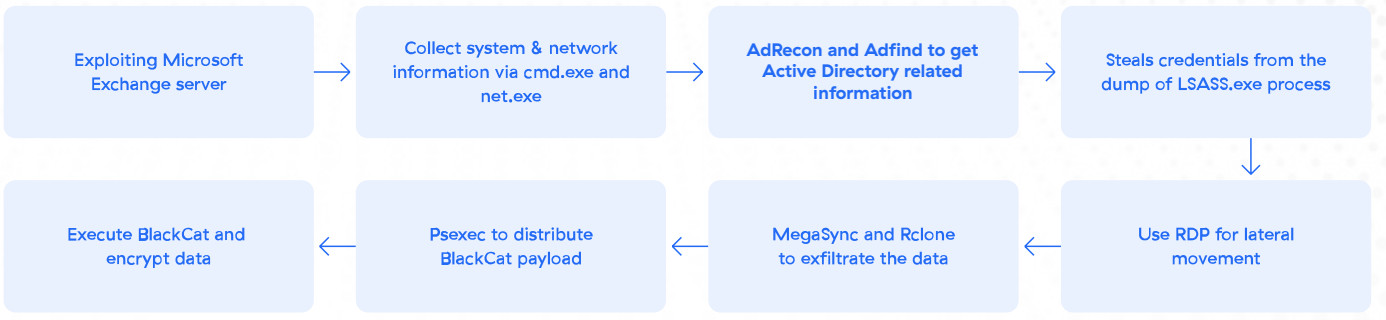
BlackCat/ALPHV infection chain
This attack demonstrates the sophistication and creativity of the BlackCat ransomware group, which constantly evolves its tactics and techniques to evade detection and maximize profits.
3. BlackCat/ALPHV infections by industry
Over the past year, BlackCat has focused its attacks on various industries, primarily the services industry, accounting for approximately 13.78% of the group’s total attacks. This sector encompasses a wide range of businesses involved in providing professional, technical, and support services.
BlackCat also directed a significant portion—approximately 12.99%—of its attacks toward the manufacturing sector. This industry includes companies engaged in the production of goods, spanning diverse sectors such as automotive, electronics, textiles, and more.
The legal industry, comprising law firms and legal services providers, was also a notable target for BlackCat, accounting for approximately 8.27% of the attacks. The attackers likely saw value in compromising sensitive legal information, client data, or intellectual property associated with law firms and their clients.
Furthermore, BlackCat showed considerable interest in targeting the financial services sector, which accounted for approximately 5.51% of the attacks. This sector encompasses banks, financial institutions, insurance companies, and other entities involved in financial transactions and services. The attackers may have sought to gain access to valuable financial data and personal information or discover other exploitable vulnerabilities in banking systems to use for scams and other forms of attack.
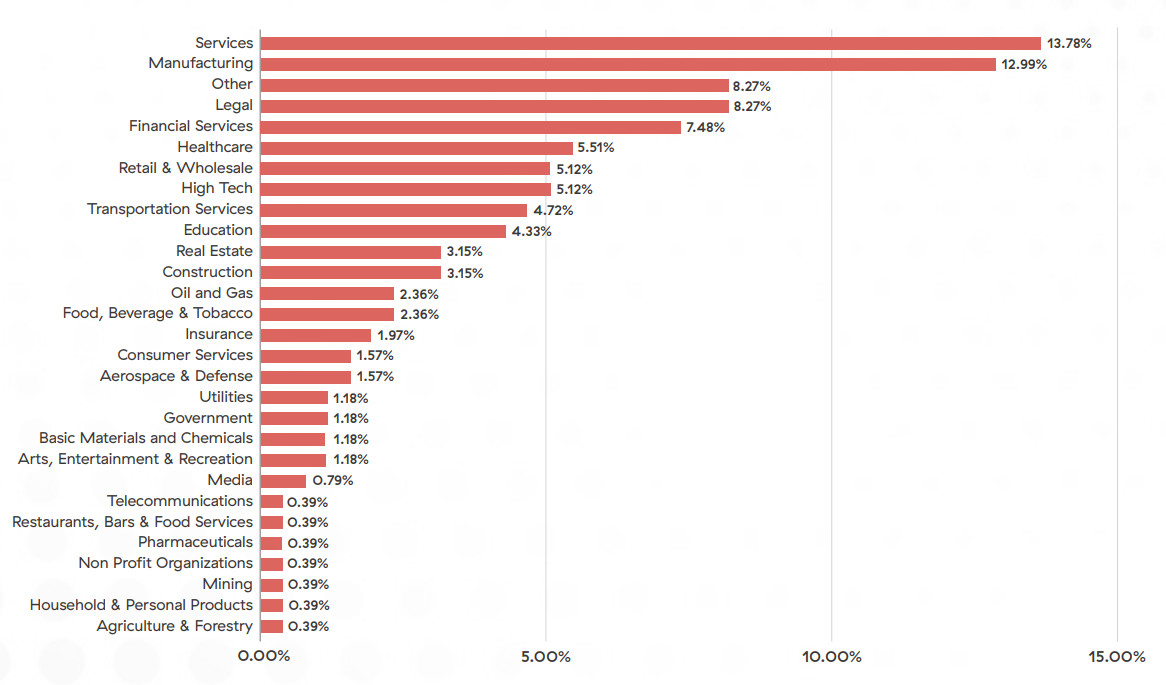
Industry verticals targeted by double extortion attacks using BlackCat
4. Blocking BlackCat/ALPHV
First, let’s illustrate our basic demo environment. The environment is running Windows 10 operating system, the disk space is about 80GB, the space occupied by the installed space is about 45GB. among them, the size of the document used for testing is about 500MB, the size of the picture used for testing is about 400MB, and the audio and video files used for testing are about 1.7GB. the size of the space of the operating system program is about 11GB, and the space of the program of the tool used for your own installation is About 3GB.

basic demo environment
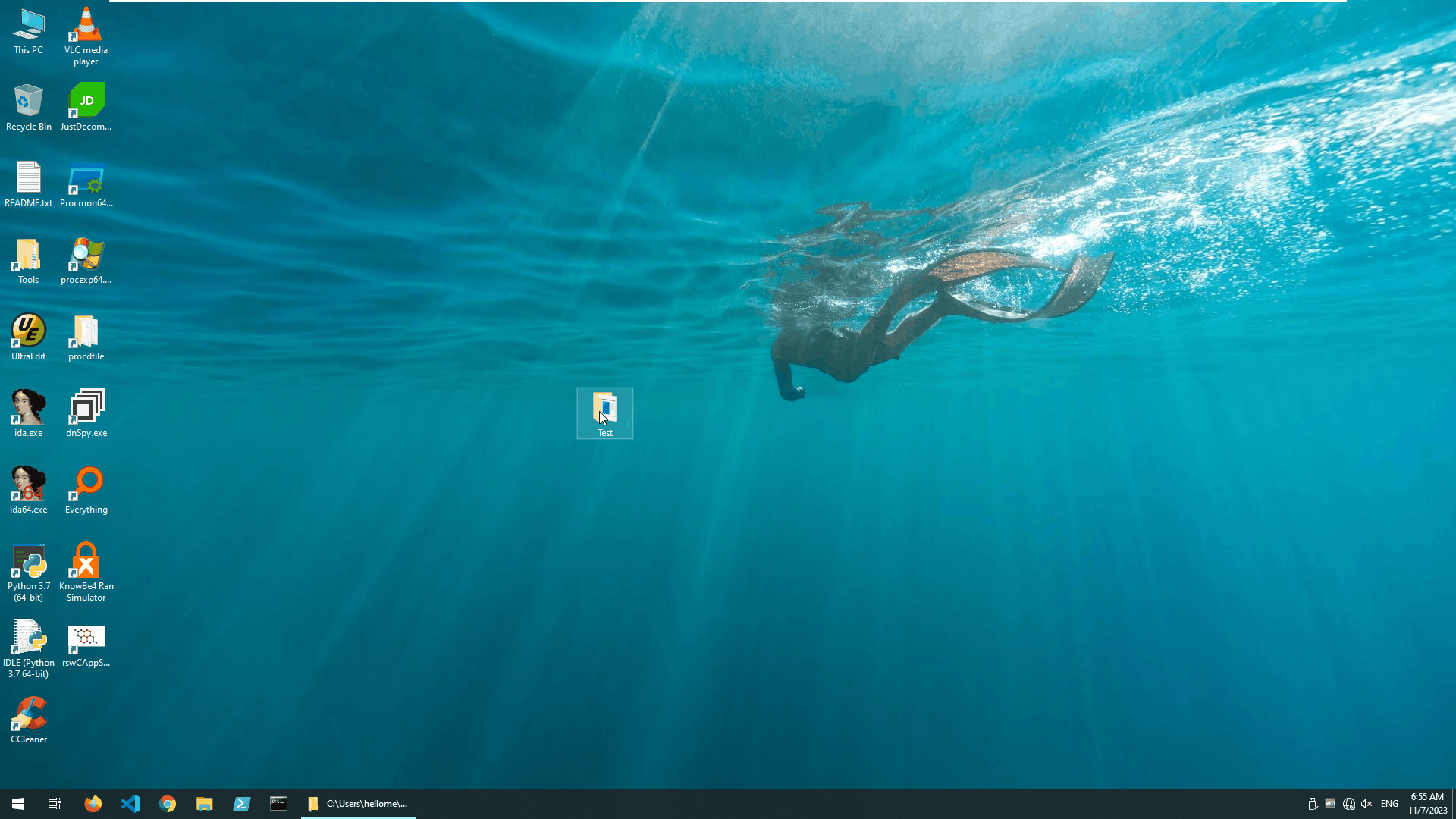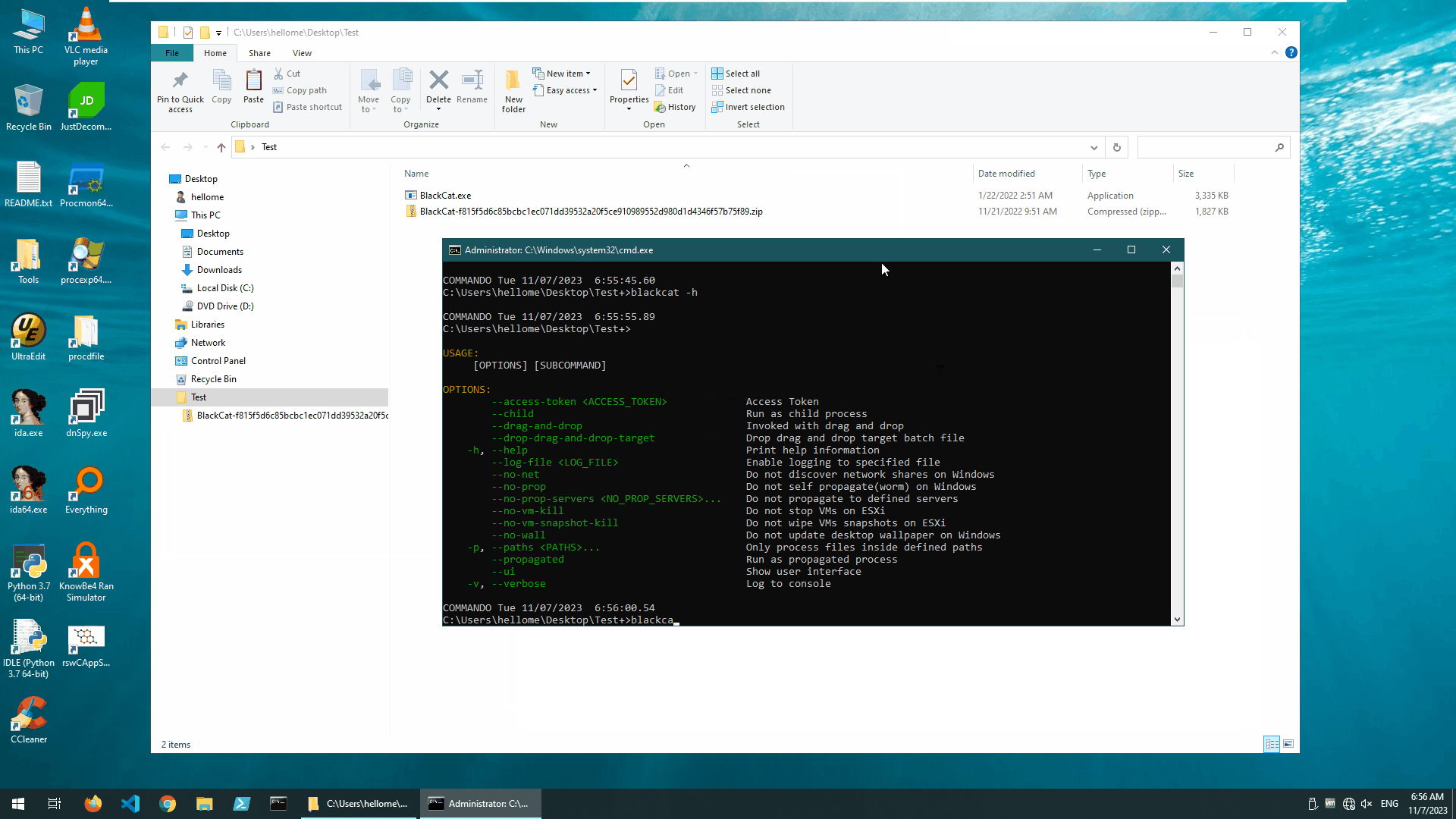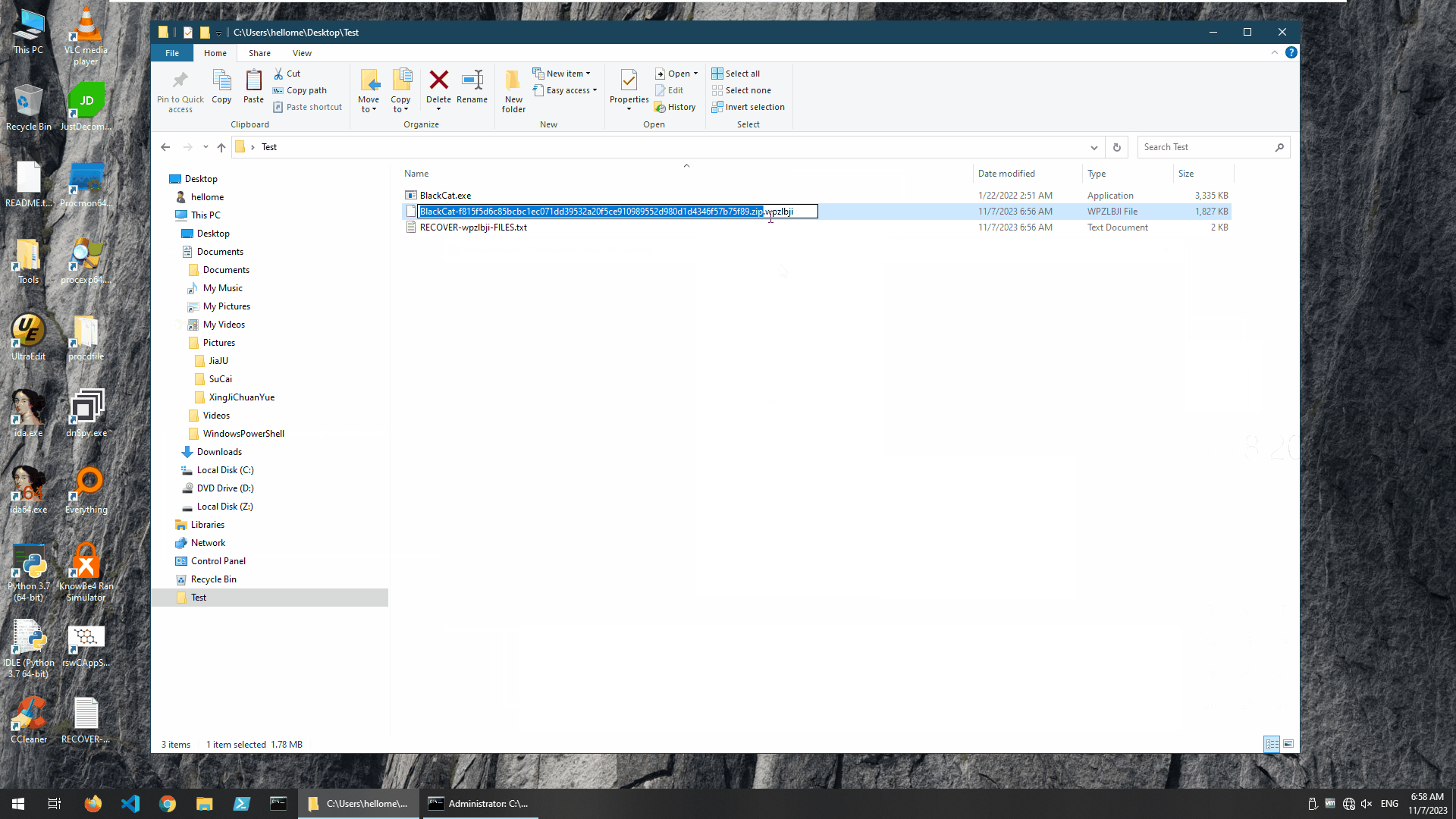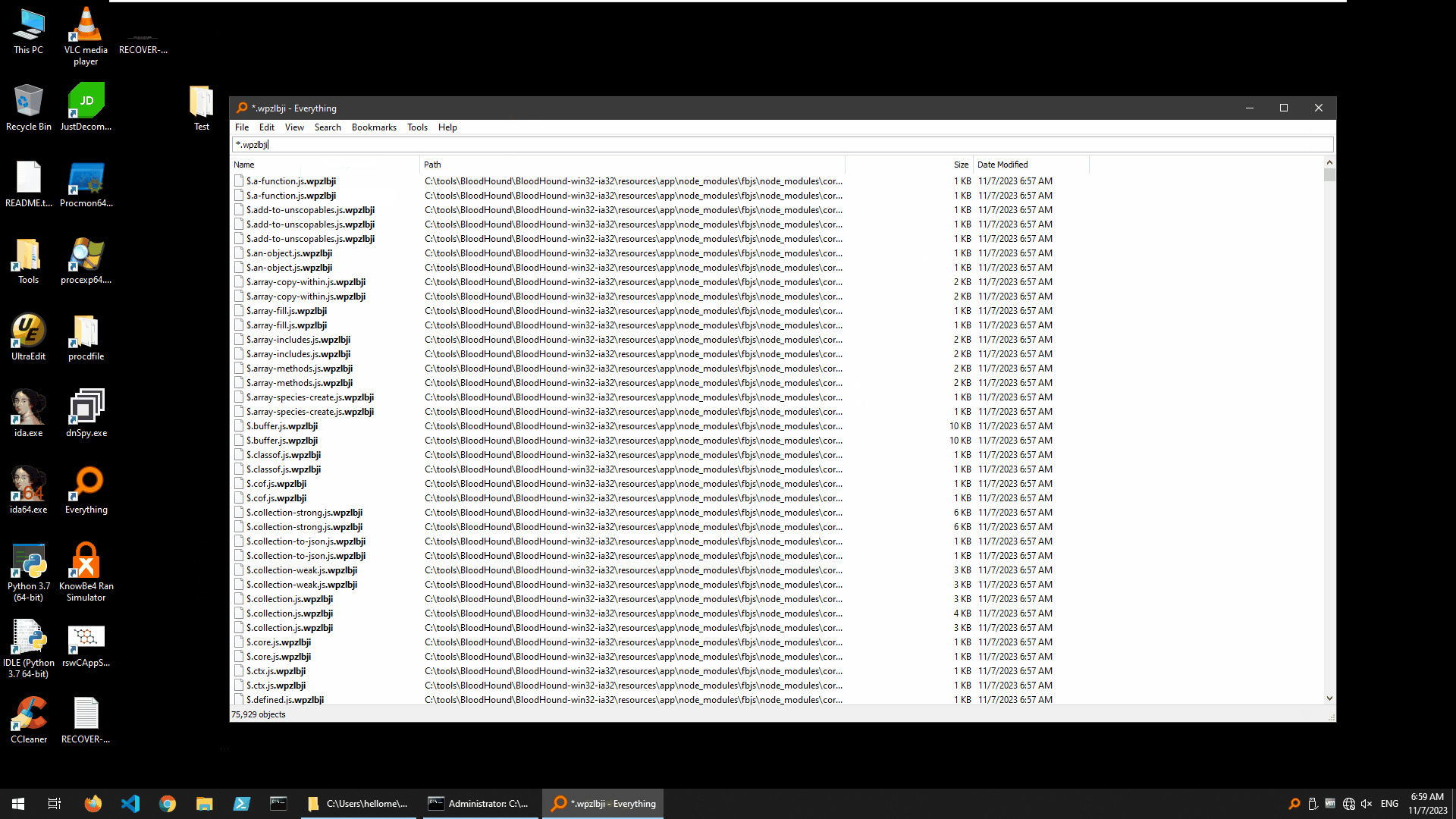
We “detonated” the BlackCat ransomware in our test environment with no protection turned on. The SHA256 value of this ransomware sample is f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89.
The operation of this ransomware requires configuration parameters that can be entered via the command line. The addition of these configuration parameters increases the variety and complexity of the operational status of this ransomware.
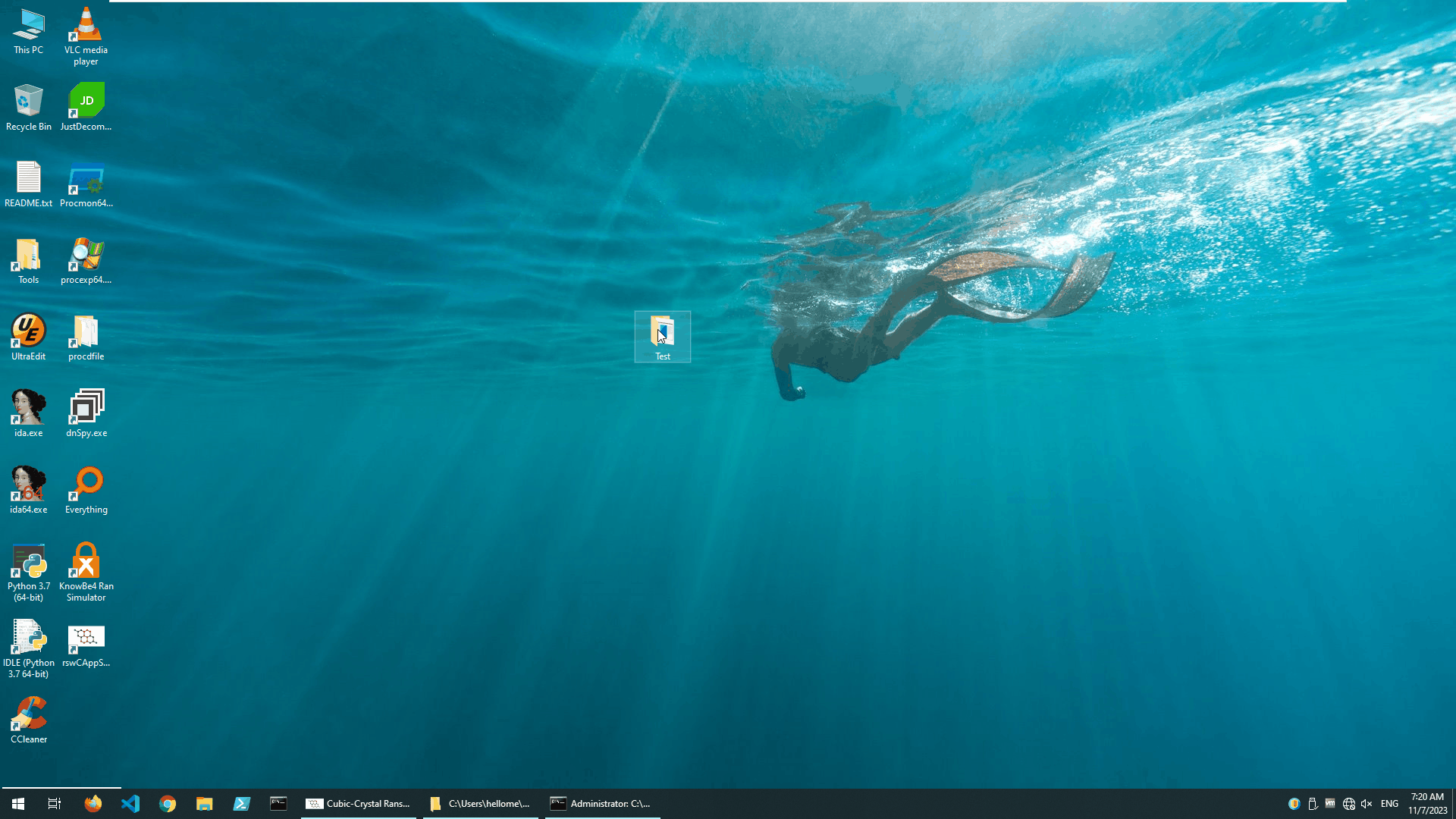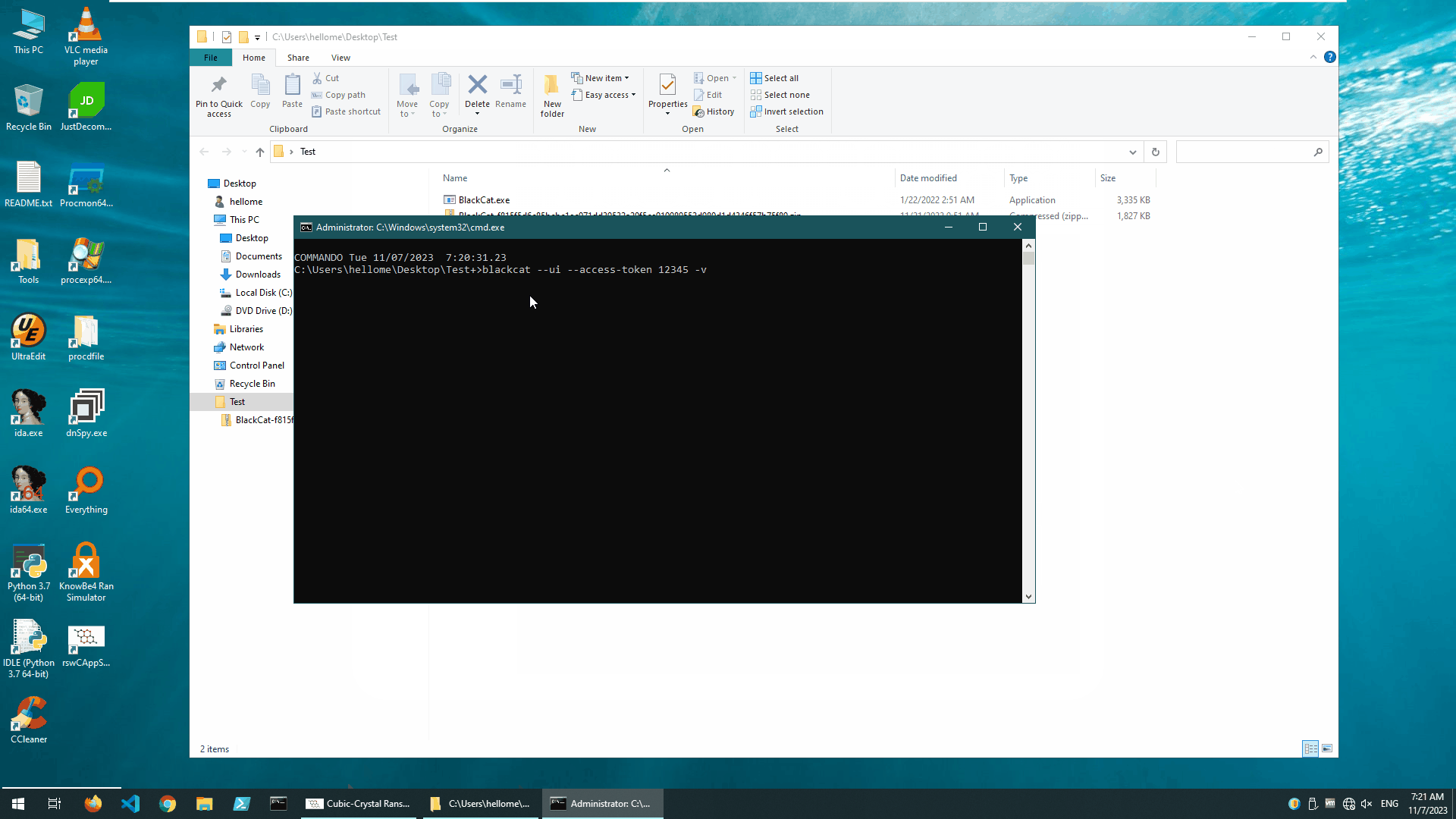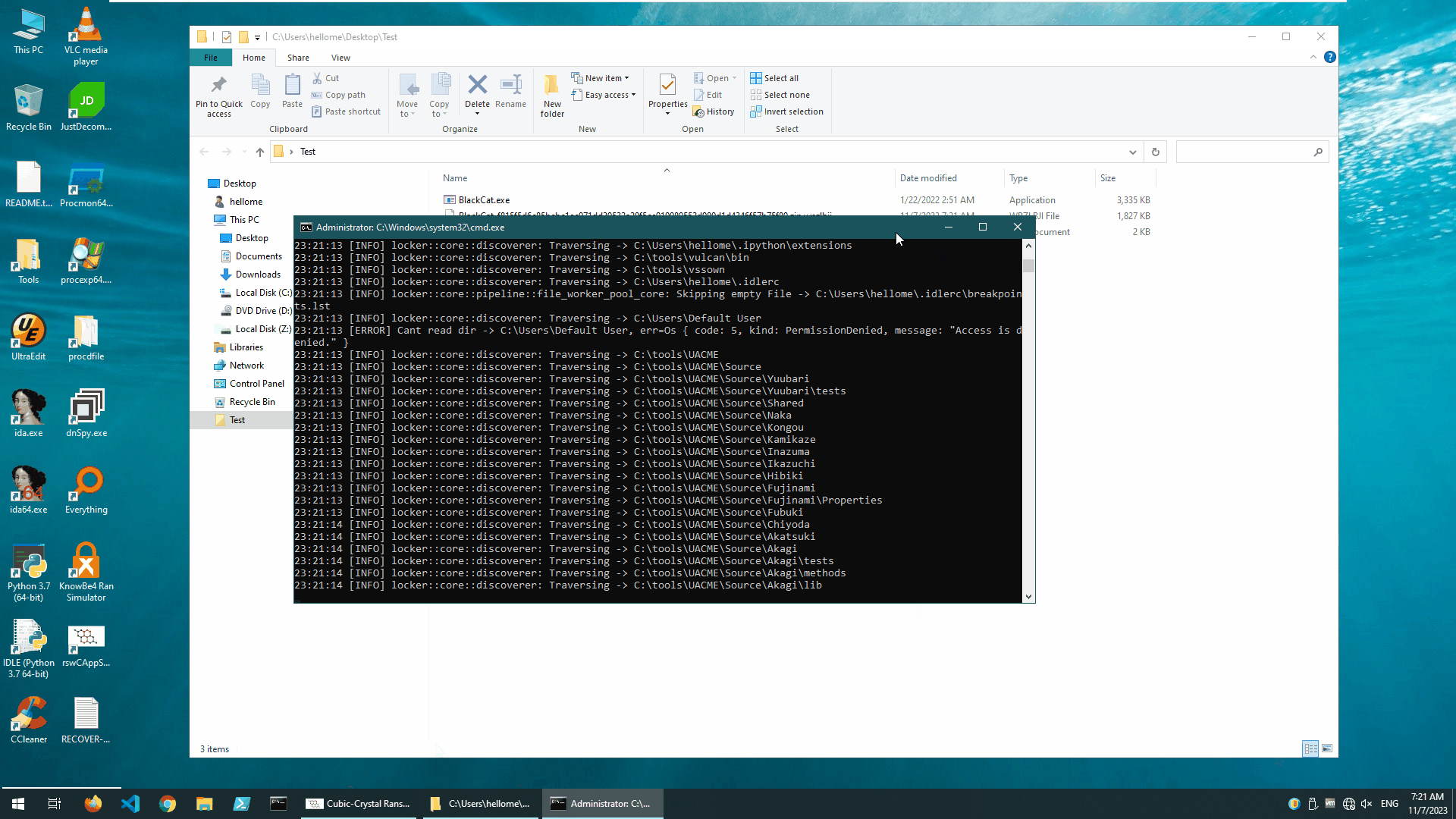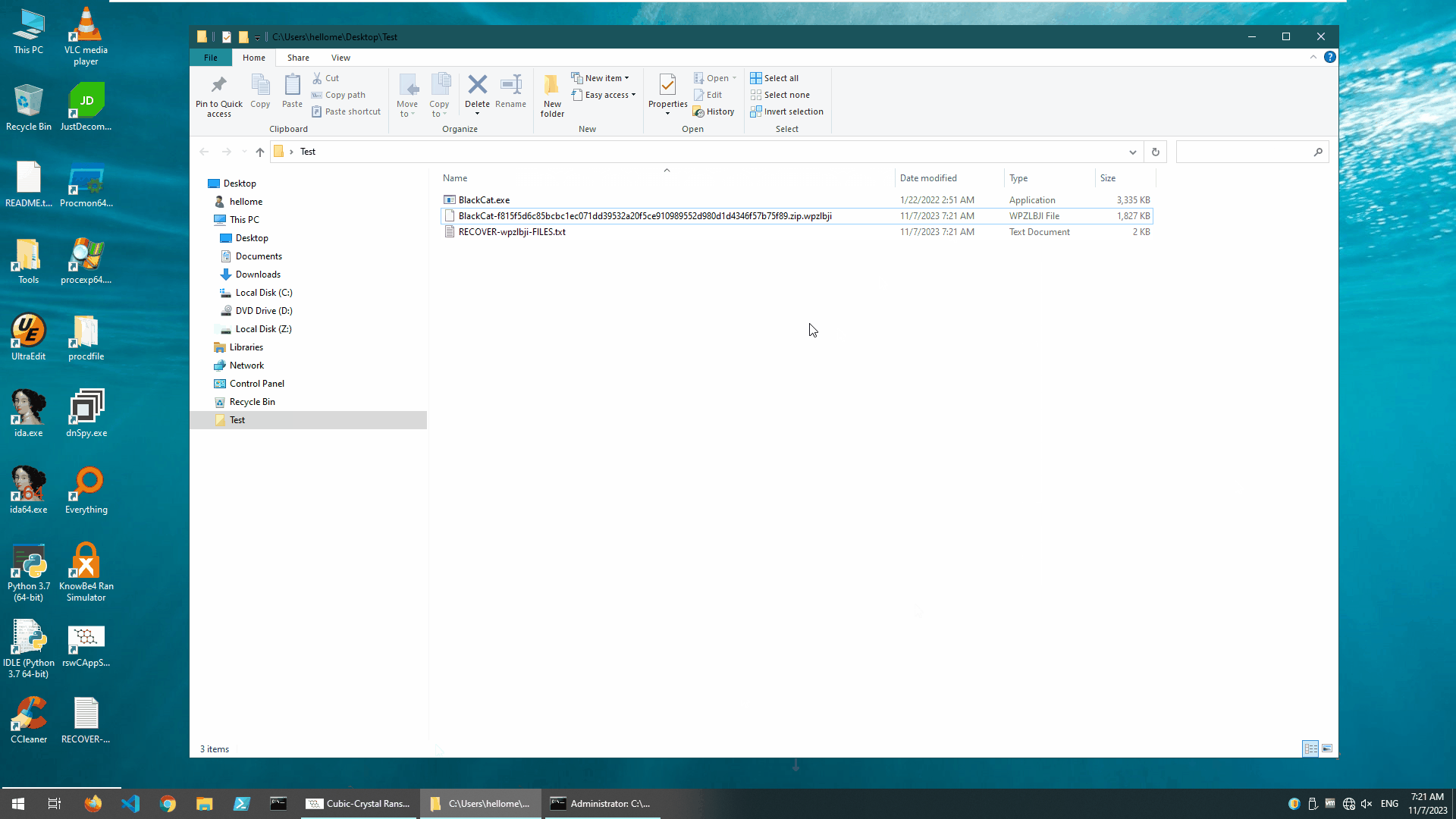
The ransomware sample completed its damage to the test environment in about 2 minute, modifies the desktop and leaves ransom messages.
It should be noted and clarified that the printouts we made through the console slowed down its execution to a great extent. In fact, this ransomware runs at a very high speed.
BlackCat encrypted unprotected system
As you can see, the ransomware sample encrypted about 76,000 files in a very short period of time.
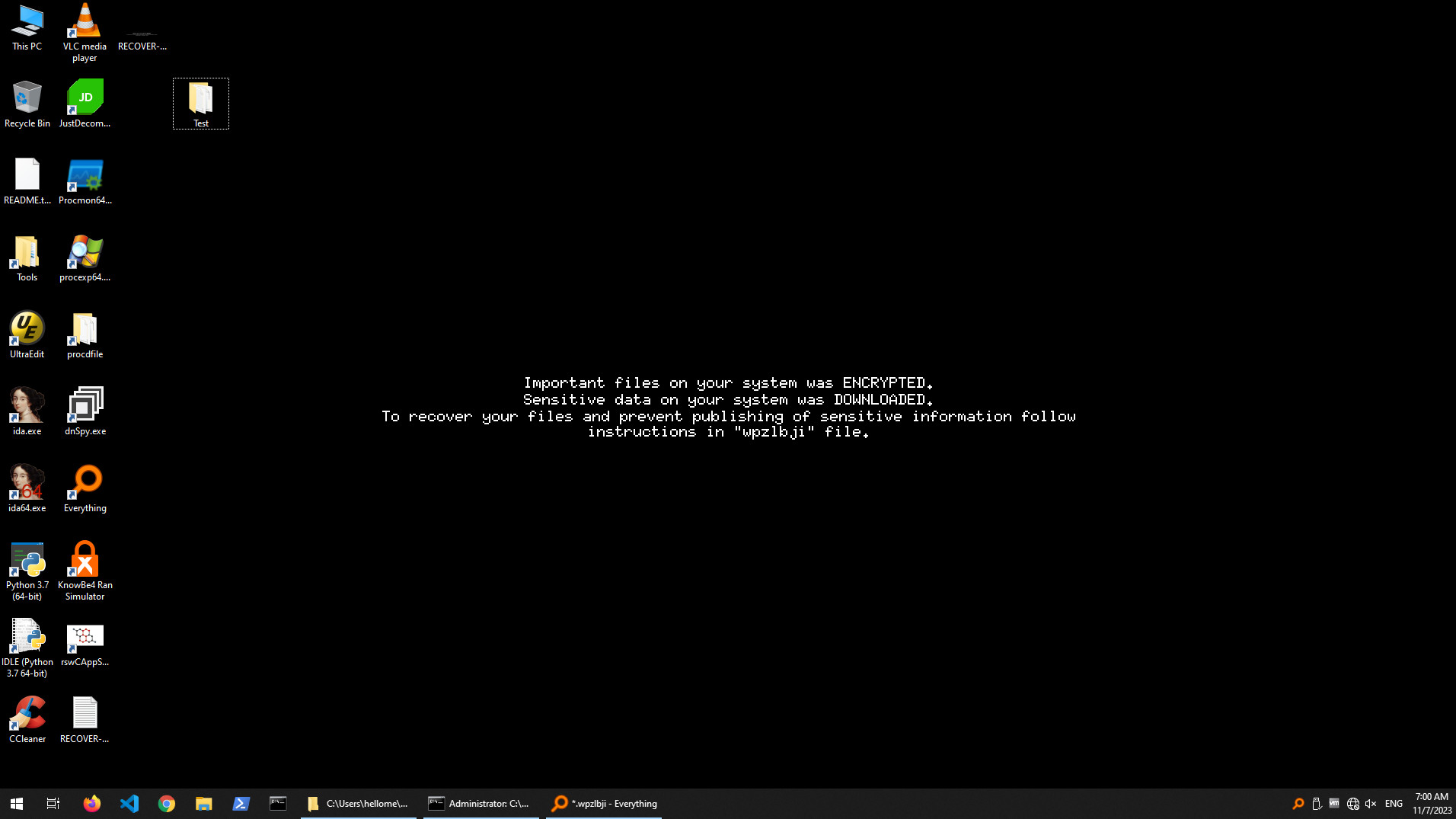
BlackCat modifies the desktop
BlackCat encrypted a lot of files
Let’s take a look at how the Cubic-Crystal®™ System blocks BlackCat ransomware.
It’s very simple: we just flipped the switch on the main engine and it only took a few milliseconds for the Cubic-Crystal®™ System to determine that it was a crypto-type ransomware and block it.In this test, we “detonated” the BlackCat ransomware 2 times.
In the first instance, the system killed the ransomware as a single process;
In the second instance, the system killed a sequence of malicious “clique” processes formed by the ransomware as a group of processes.
Blocking BlackCat Ransomware
Let’s check how many files we have lost in order to determine that this is a ransomware.
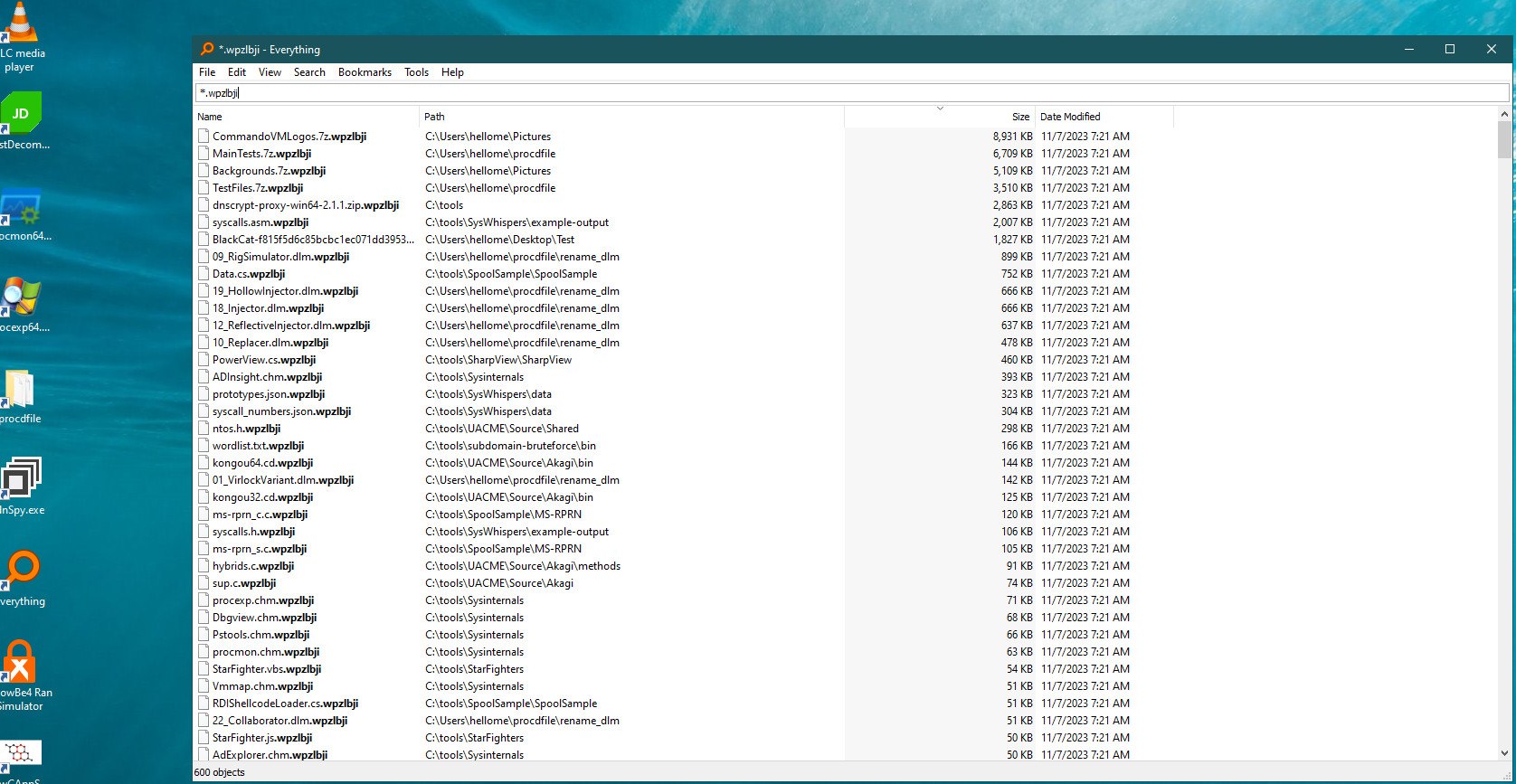
We lost 600 files
Yes, we lose files to determine if a process or group of processes is malicious ransomware. Remember, Cubic-Crystal®™ System is not based on file checksums or signature codes but a behavior-based ransomware monitoring and blocking system. Because of this technical feature, it has the ability to protect ourselves against unknown ransomware.
We lost 600 files, an average of 300 at a time. And, don’t worry, the system automatically backs up most of them.
Using Cubic-Crystal®™ System is very effective !
Remember our slogan: Fighting ransomware with cryptography !