Blocking LockBit with Cubic-Crystal System
By Beijing Mike
1. LockBit ransomware
LockBit ransomware first emerged in September 2019 and quickly became one of the most active and notorious threat groups ThreatLabz followed. The past year saw some significant developments, with two new versions of the ransomware.
In June 2022, the group released LockBit 3.0 (a.k.a. LockBit Black, because it shares code with the defunct BlackMatter ransomware). In September 2022, the LockBit 3.0 builder was leaked. After the leak, several other ransomware groups including SchoolBoys and the Bl00dy ransomware gang used the builder to create and launch their own ransomware campaigns. In January 2023, the group created LockBit Green, which is based on the leaked Conti source code. In April 2023, the group appeared to have developed ransomware for macOS, although the code was still rather primitive. Over the past year, LockBit started leaking chat logs from victims that refused to pay ransoms. One such set of logs, involving the Royal Mail Group in the UK, revealed the ransom demand was set at US$80 million based on 0.5% of the postal service’s revenue. This is one of the largest ransom demands ThreatLabz has ever observed.
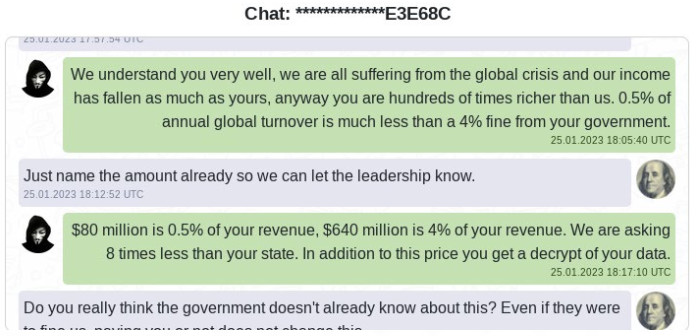
Leaked chat logs from the Royal Mail Group with a US$80M ransom
Over the past year, LockBit also introduced a bug bounty program, encouraging researchers to report bugs for $1,000 to $1 million bounties.
Screenshot of LockBit bug bounty program
LockBit leverages a large affiliate network to conduct breaches, exfiltrate data, and deploy its ransomware. Some of these affiliates break into organizations through spam emails that contain malicious attachments or links. Others have leveraged brute force password attacks targeting Remote Desktop Protocol (RDP) or VPN credentials, purchased compromised stolen credentials through initial access brokers, performed drive-by downloads, and exploited public-facing applications.
2. LockBit infection chain
The following is a detailed account of an attack conducted by a LockBit affiliate. The initial compromise in this attack began with the victim unknowingly accessing a compromised website, triggering a drive-by download of SocGholish malware, disguised as a software update. Once executed, SocGholish downloaded a Cobalt Strike beacon (a popular post-exploitation tool) and utilized PowerShell to gather system and domain information.
To evade detection and ensure a smooth, unhindered encryption process, the threat actor deployed a batch script that terminated various processes and services associated with antivirus software, databases, backups, and other programs that could potentially impede the encryption of files.
Further, the attacker used tools such as Seatbelt and BloodHound to gather additional system information. Seatbelt is a reconnaissance tool used to extract data about user accounts, local groups, security policies, and more. BloodHound assists in identifying and exploiting Active Directory vulnerabilities.
With this information and an established foothold, the threat actor employed PsExec for lateral movement, enabling them to traverse across the victim’s network and gain access to other systems. This lateral movement technique facilitated the spread of the attack within the compromised network.
To exfiltrate the victim’s data, the attacker employed MegaSync, a file synchronization tool that allowed for the transfer of stolen information to an external location under the attacker’s control.
Finally, in the last stage of the attack, the attackers deployed and executed the LockBit ransomware. This malicious software encrypted the victim’s files, rendering them inaccessible until a ransom was paid.
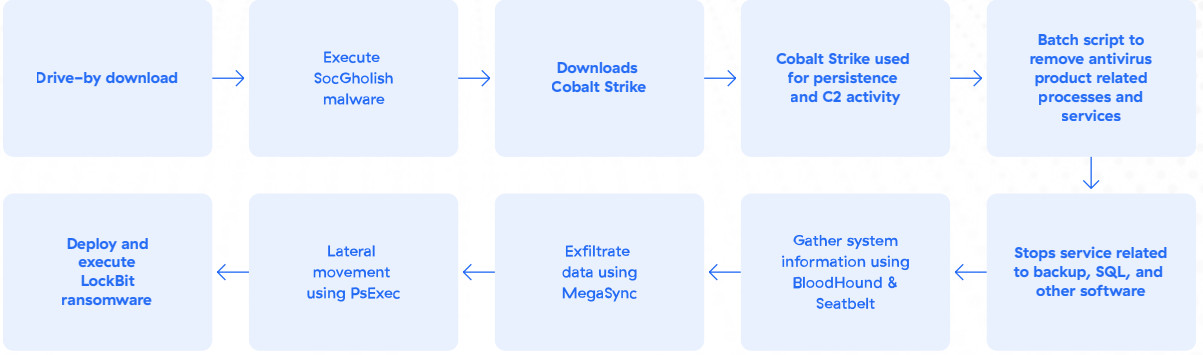
LockBit infection chain, including data exfiltration and file encryption
3. LockBit infections by industry
LockBit has consistently targeted various industries, with the manufacturing sector being the primary target over the past year, accounting for approximately 15.35% of LockBit’s total attacks. This sector includes a broad range of businesses involved in the production of goods across fields such as automotive, electronics, textiles, and more. The focus on this industry suggests that LockBit aims to exploit vulnerabilities in critical supply chains, disrupt operations, and potentially gain access to valuable intellectual property.
Significant attacks by LockBit on the services industry accounted for approximately 12.71% of the attacks. This industry encompasses a wide array of professional, technical, and support service providers, making it an attractive target for LockBit to exploit sensitive client data, financial information, and intellectual property.
LockBit also directed approximately 7.43% of its attacks at the construction sector, which includes construction companies, contractors, and related businesses involved in building infrastructure and structures. Targeting of this industry suggests LockBit may aim to disrupt ongoing projects, compromise project plans, or gain access to valuable project data.
Additionally, the retail and wholesale sector faced a substantial 6.77% of LockBit’s attacks. This sector encompasses businesses involved in the sale of goods to consumers or through wholesale distribution. LockBit’s targeting of this sector may stem from a desire to compromise customer data, financial information, or disrupt business operations.
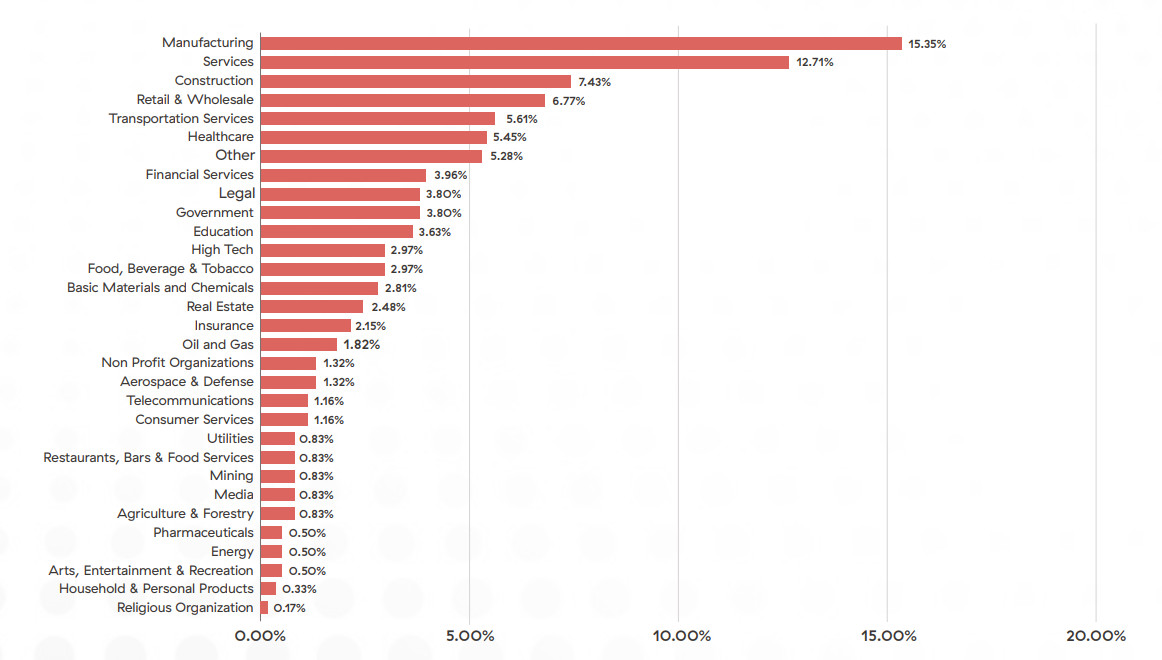
Industry verticals targeted by double extortion attacks using LockBit
4. Blocking LockBit
First, let’s illustrate our basic demo environment. The environment is running Windows 10 operating system, the disk space is about 80GB, the space occupied by the installed space is about 45GB. among them, the size of the document used for testing is about 500MB, the size of the picture used for testing is about 400MB, and the audio and video files used for testing are about 1.7GB. the size of the space of the operating system program is about 11GB, and the space of the program of the tool used for your own installation is About 3GB.

basic demo environment
We “detonated” the LockBit2 ransomware in our test environment with no protection turned on. The SHA256 value of this ransomware sample is 2ba9fab56458fe832afecf56aae37ff89a8b9a494f3c2570d067d271d3b97045.
The ransomware sample completed its damage to the test environment in about 1 minute, leaving a note demanding ransom information.
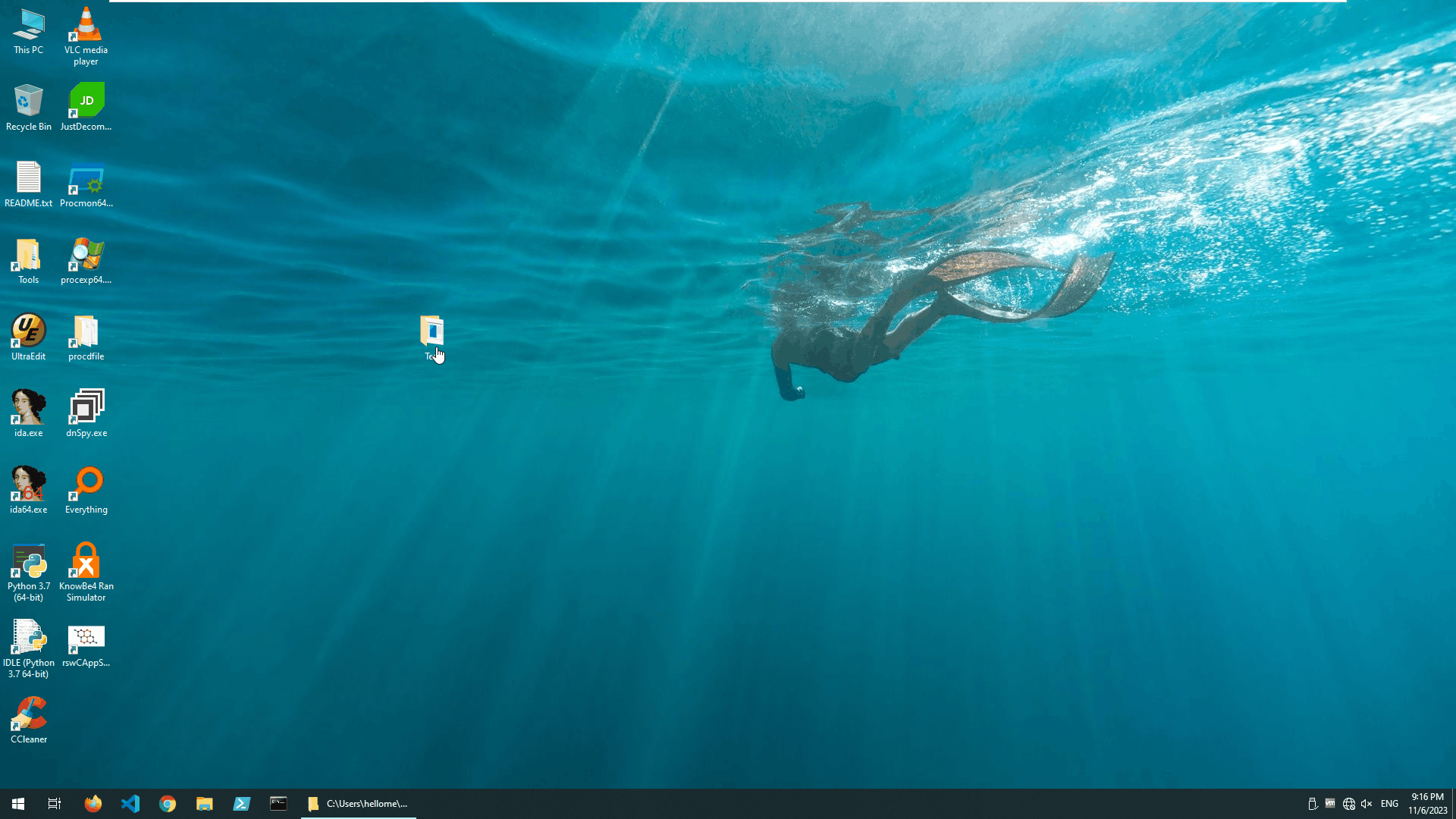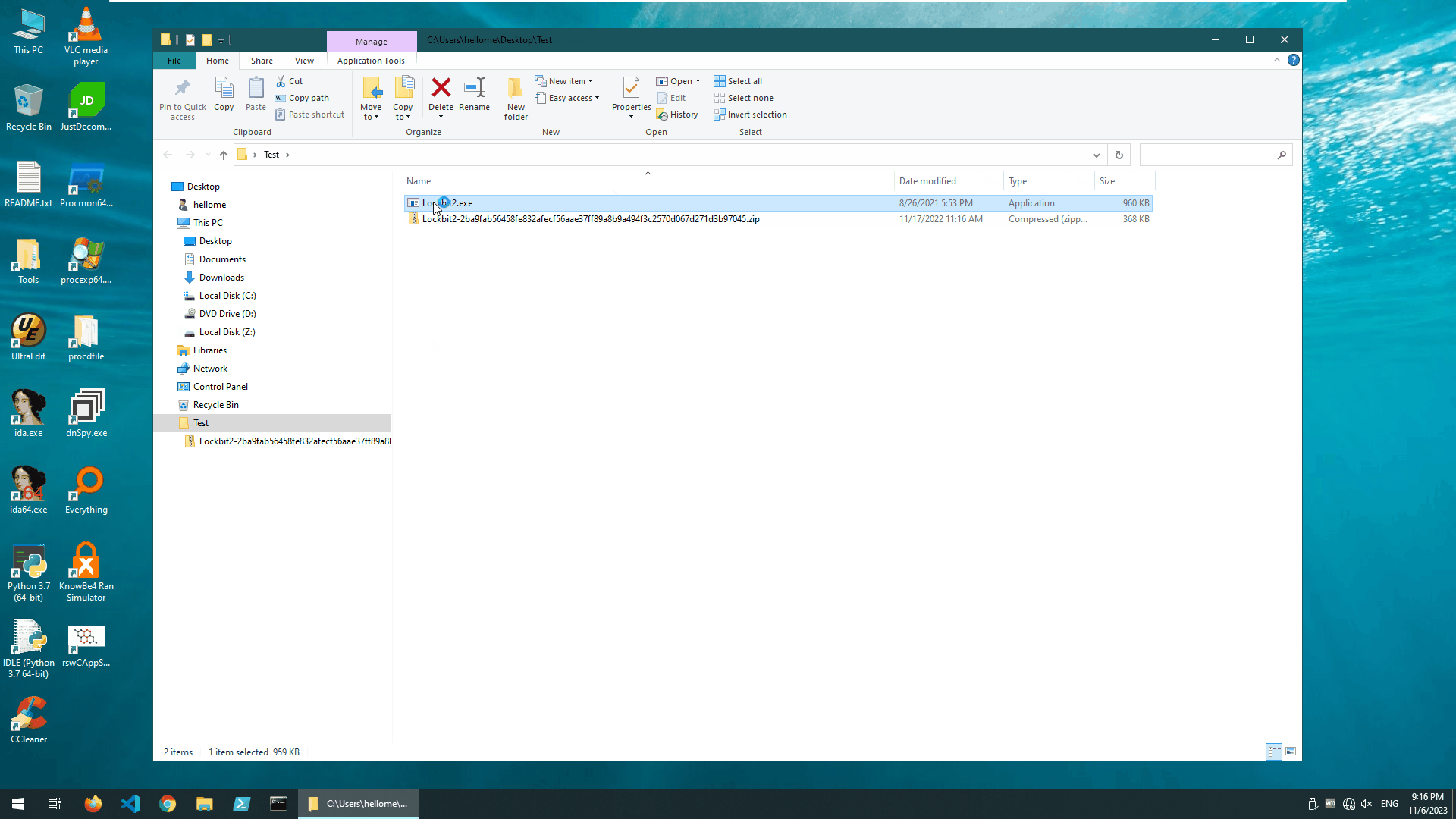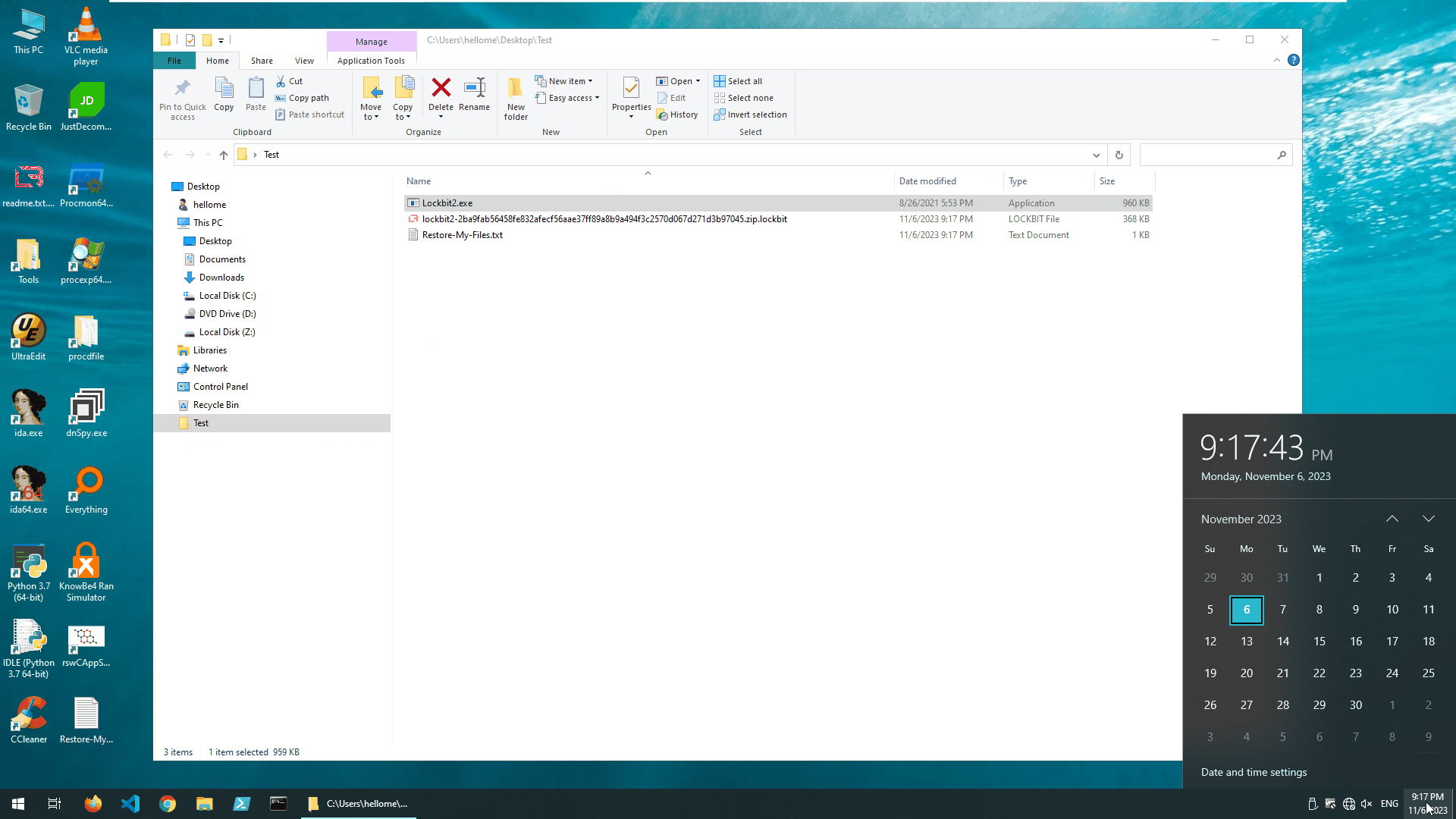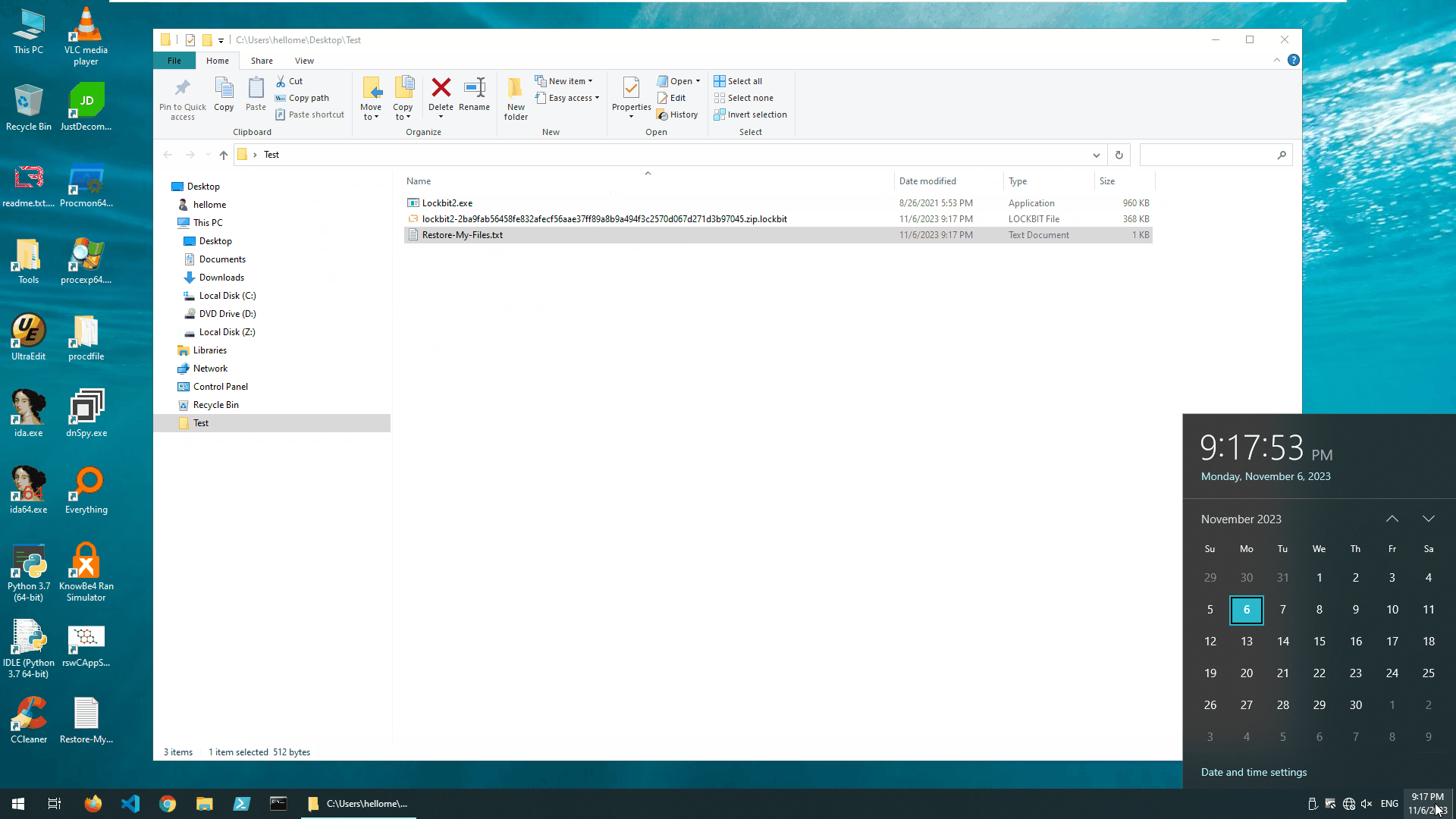
LockBit2 encrypted unprotected system
As you can see, the ransomware sample encrypted about 110,000 files in a very short period of time.
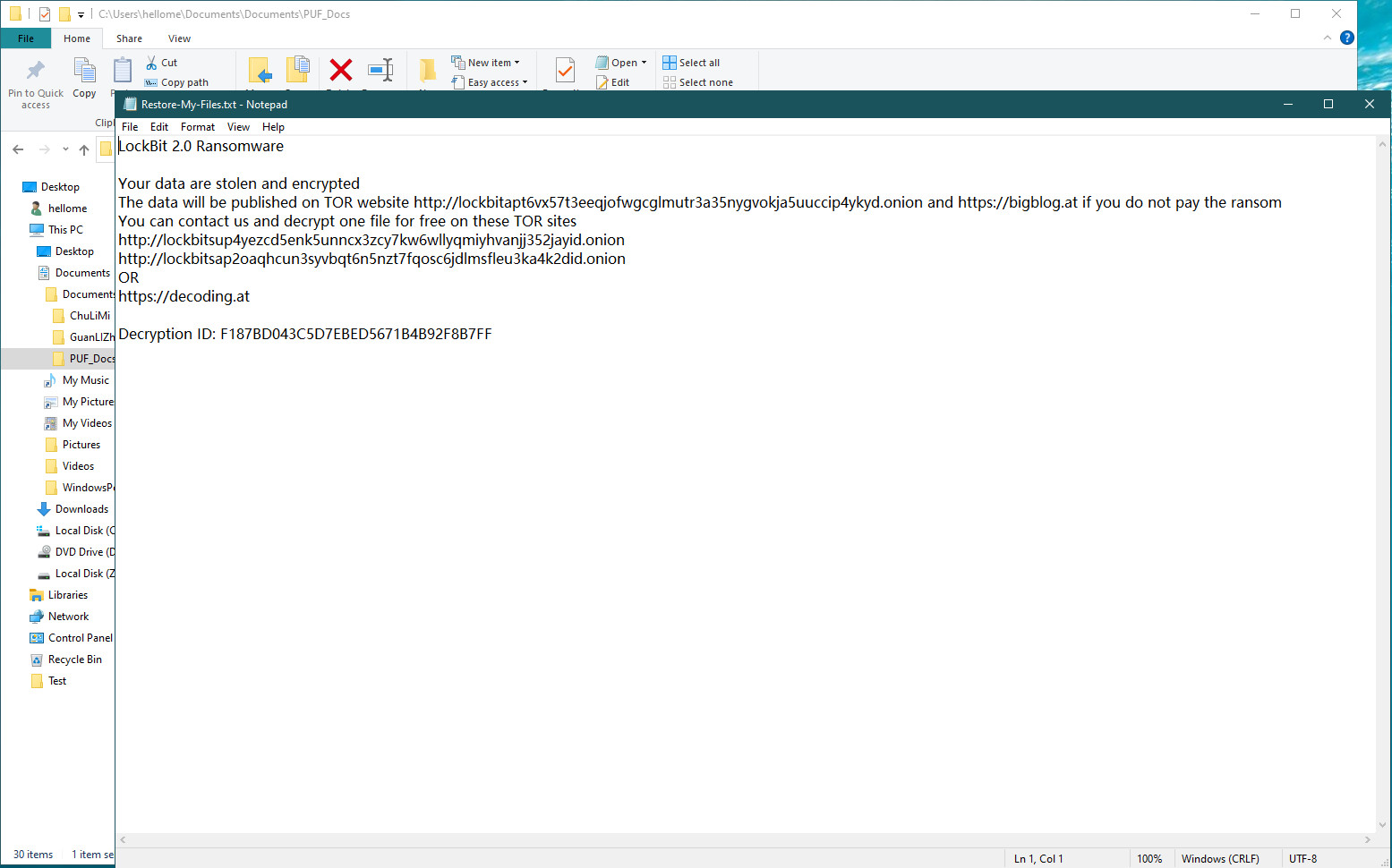
LockBit2 leaves a ransom note
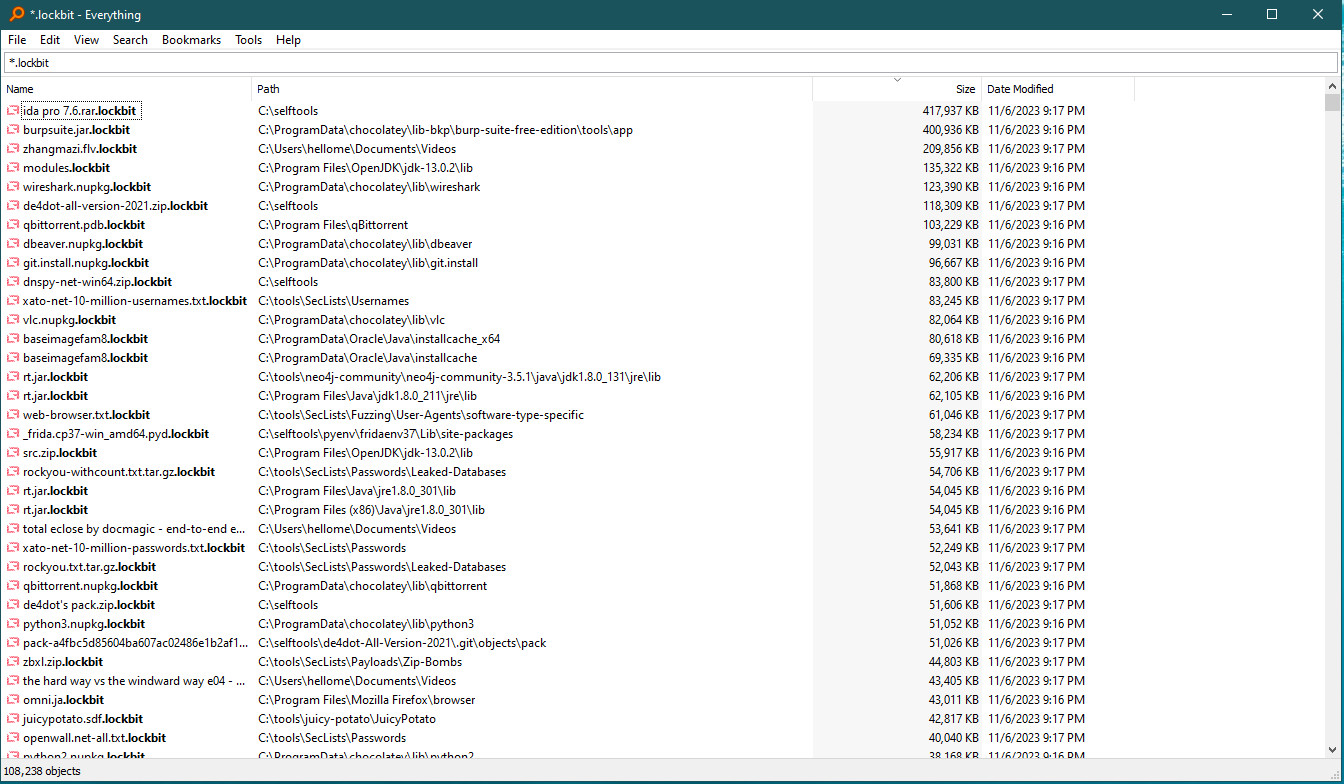
LockBit2 encrypted a lot of files
Let’s take a look at how the Cubic-Crystal®™ System blocks LockBit ransomware.
It’s very simple: we just flipped the switch on the main engine and it only took a few milliseconds for the Cubic-Crystal®™ System to determine that it was a crypto-type ransomware and block it.In this test, we “detonated” the LockBit ransomware 2 times.
In the first instance, the system killed the ransomware as a single process;
In the second instance, the system killed a sequence of malicious “clique” processes formed by the ransomware as a group of processes.
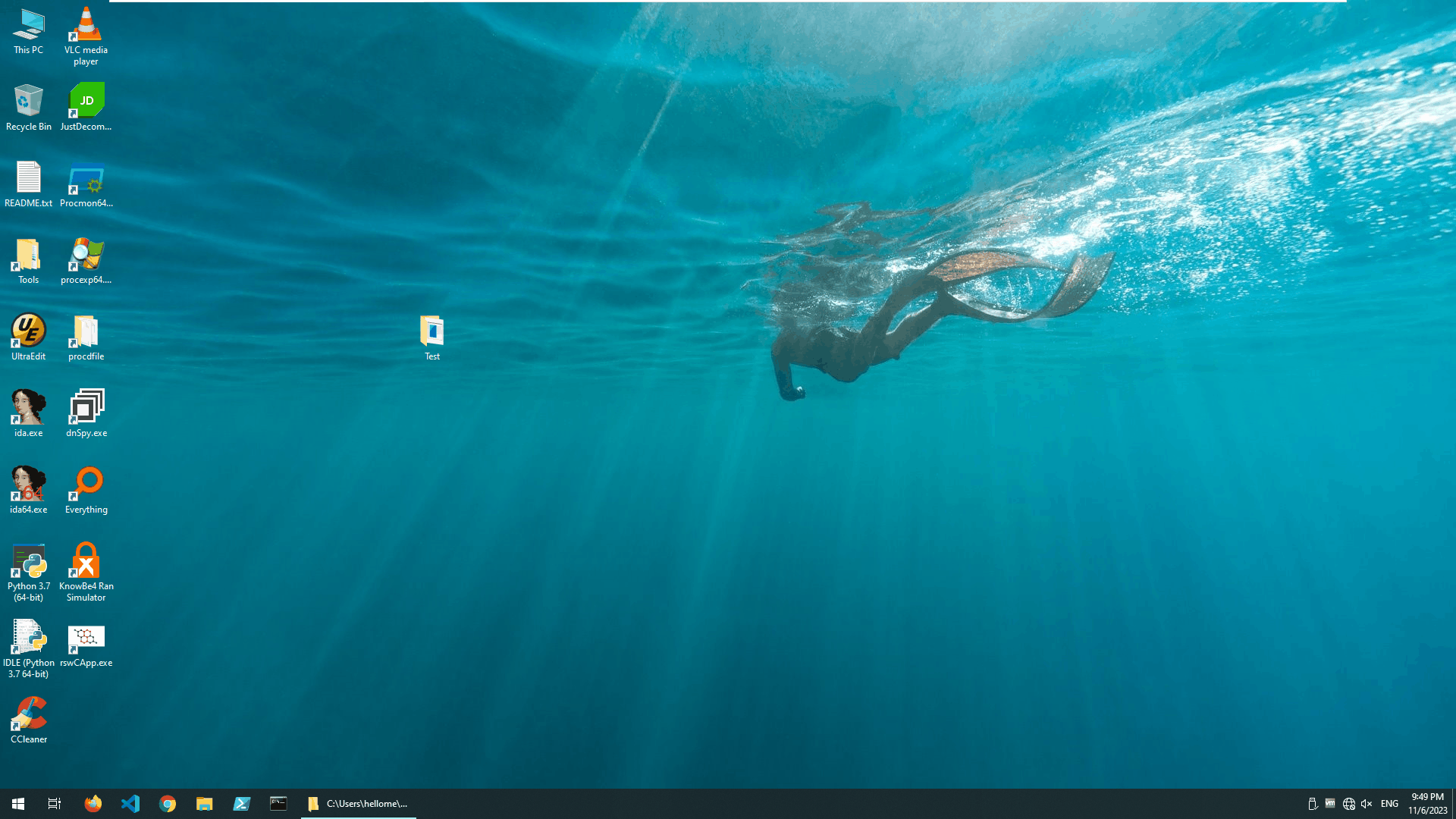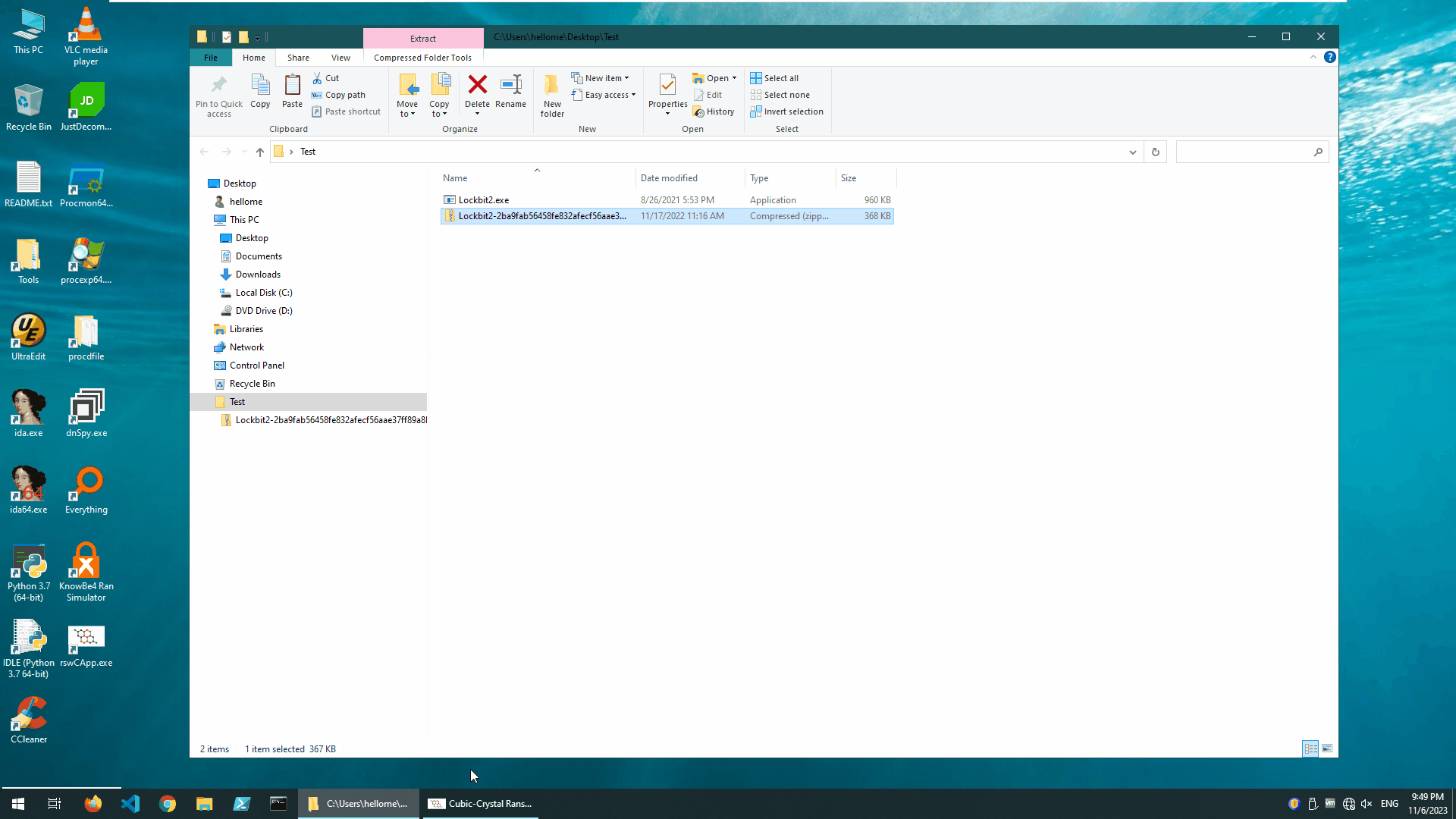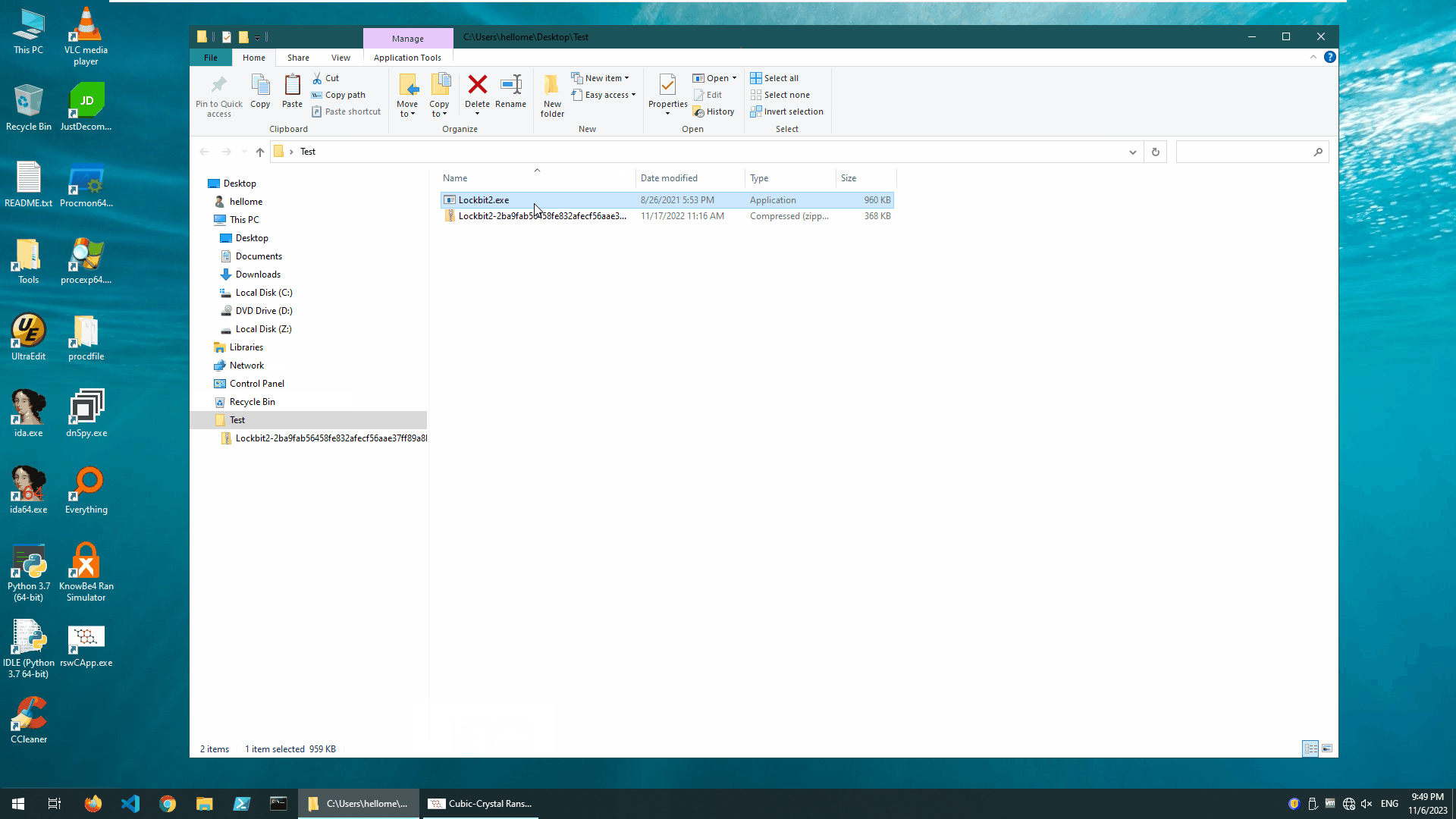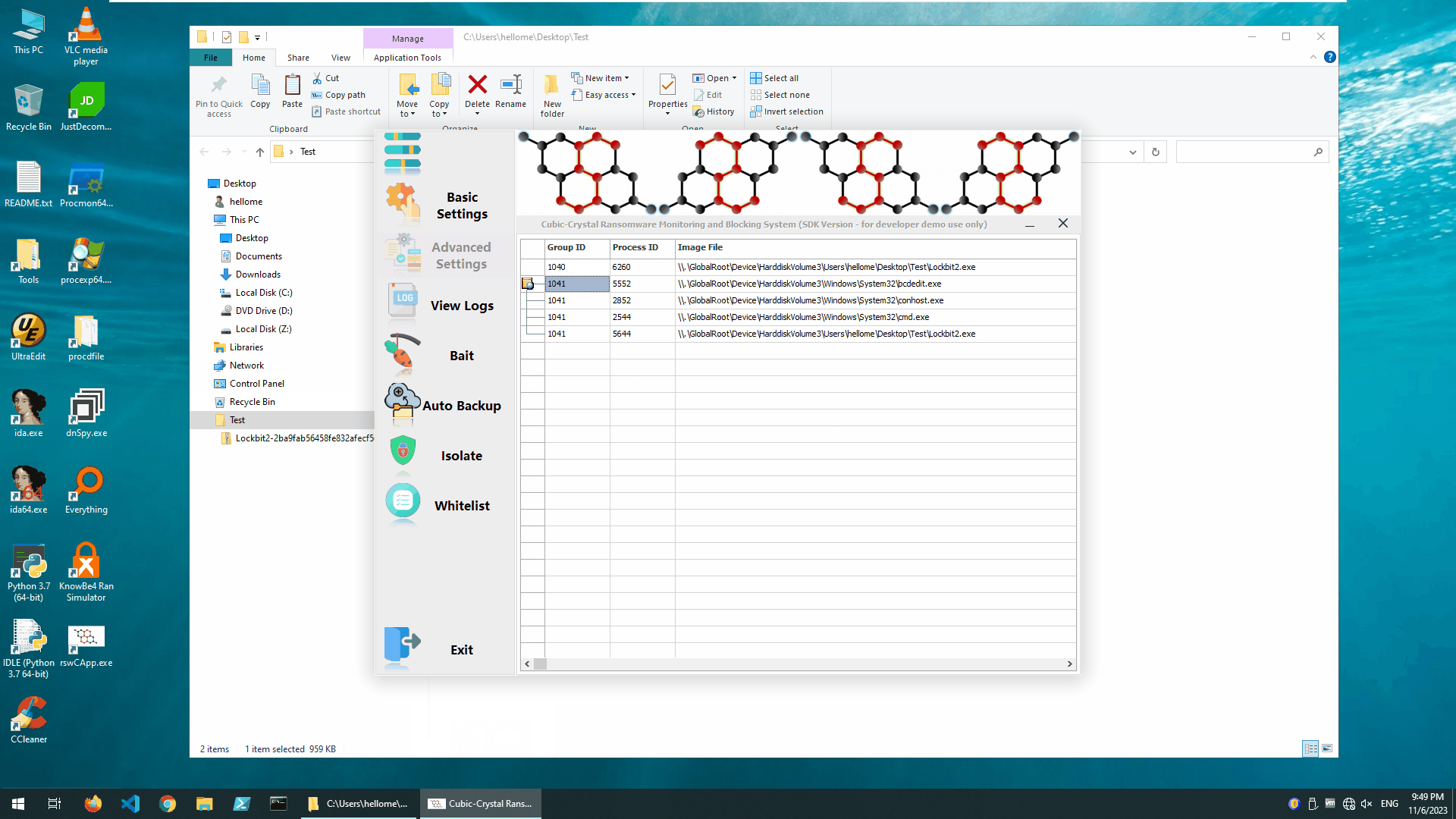
Blocking LockBit Ransomware
Let’s check how many files we have lost in order to determine that this is a ransomware.
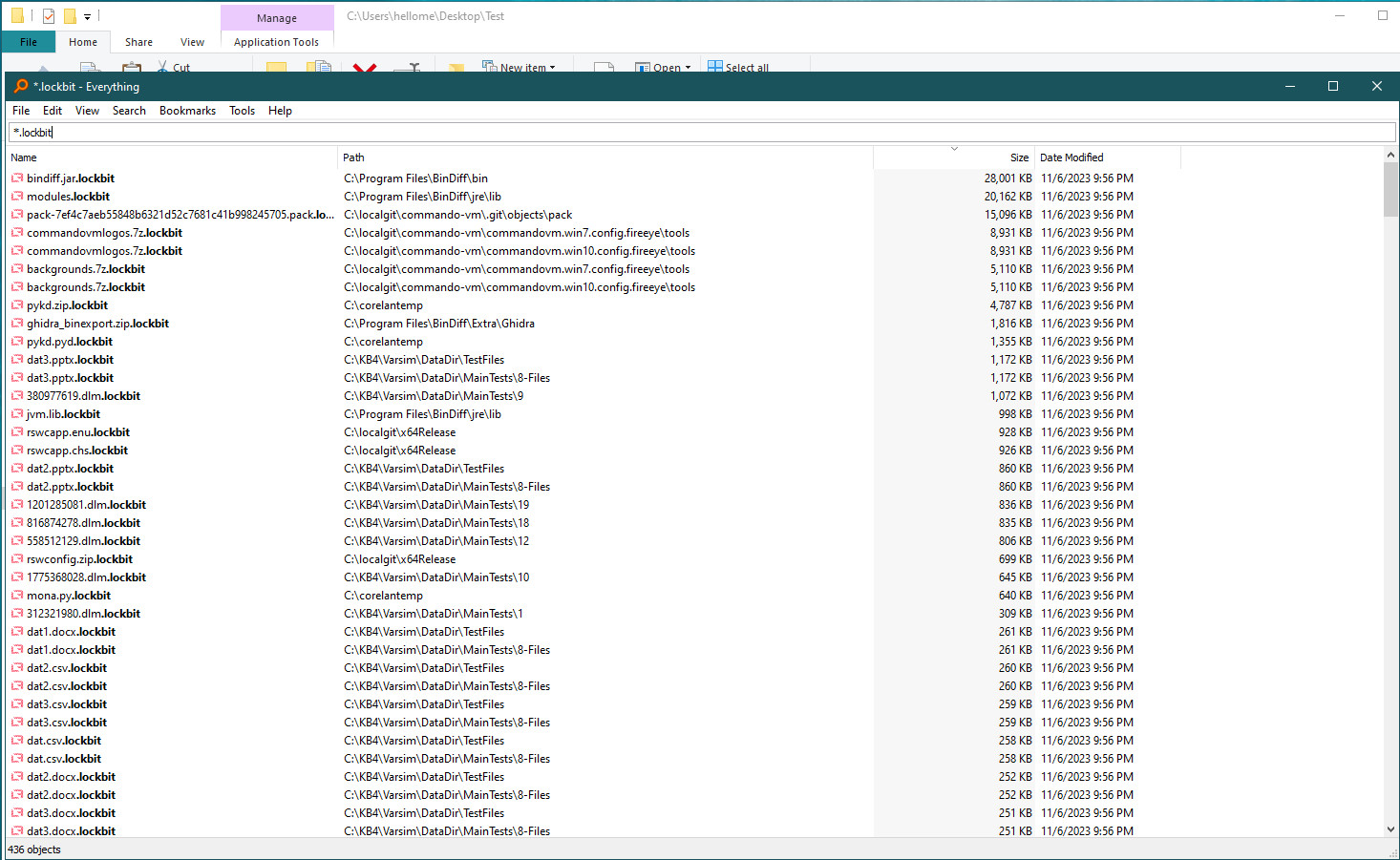
We lost 436 files
Yes, we lose files to determine if a process or group of processes is malicious ransomware. Remember, Cubic-Crystal®™ System is not based on file checksums or signature codes but a behavior-based ransomware monitoring and blocking system. Because of this technical feature, it has the ability to protect ourselves against unknown ransomware.
And users don’t have to worry too much, Cubic-Crystal®™ System automatically backs up most of these files.
Using Cubic-Crystal®™ System is very effective!
Remember our slogan: Fighting ransomware with cryptography!