Technical comparisons with antivirus systems
By Beijing Mike
1. Technical comparisons
The design concept of Cubic-Crystal®™ Ransomware Monitoring and Blocking System is “Fighting ransomware with cryptography”, and its core realization principle is to determine whether there is any malicious file encryption behavior through the monitoring of the file system, which is an essential feature of ransomware and cannot be hidden or changed.
The ransomware discrimination method used by antivirus systems is mainly feature recognition, which is triggered when features such as file fingerprints (hashes) and command fingerprints are determined. It can be used to check and kill known ransomware with unchanged features, and requires the support of a larger and real-time updated virus database.
In addition, due to the common use of modern malware logic obfuscation, file shelling and other technologies, even the same family of malware is ever-changing, and now more than 300,000 types of new malware are generated every day.
For antivirus systems they are always passively “finding and catching up” with those ransomware, unable to effectively respond to 0day attacks.
Especially if the antivirus system is not connected to the Internet or the virus database is not updated in time, the protected system will be exposed to greater security risks.

A large number of ransomware will appear every day
The conventional whitelist control mechanism determines whitelist compliance and decides whether to allow the program to execute by using the executable program’s file name, location, checksum value, signature value and other information.
In modern malware, process injection, process hiding, system-level HOOK and other techniques are widely used, especially new attack methods such as scripting attacks and fileless attacks, which poses new threats to whitelist-based control mechanism.
Because the whitelist control mechanism is unable to perform continuous monitoring after the process is running, it also cannot solve the problem of legitimate processes being contaminated or critical functions being hijacked and replaced.
Cubic-Crystal®™ Ransomware Monitoring and Blocking System, in contrast, adopts a discrimination technology based on the principle of cryptography, i.e., if a file is encrypted, its complexity (also known as the “entropy” value) is bound to change, and this change has a lot of temporal and spatial characteristics, which can be statistically counted by mathematical methods and discriminated by specific algorithms.
Such relevant characteristics are the essential traits of ransomware that are bound to exist, no matter how ransomware changes its coding fingerprints or program logic. These characteristics are also ransomware to achieve the goal “make the ransomed person lose important data to complete the ransom”.
Therefore, Cubic-Crystal®™ system has the ability to prevent unknown ransomware with ever-changing fingerprints, especially the new ransomware that uses a certain 0day attack technique.
At the same time, because Cubic-Crystal®™ system completes ransomware identification through specific algorithms, that doesn’t rely on feature libraries, runs independently without central support, and has unchanged logical implementation until there is a new breakthrough in ransomware technology, it does not need to be connected to the network for updating or controlled by the center, and can be deployed independently to maintain a normal working condition for a long period of time.
This ransomware monitoring and blocking system can prevent known and unknown ransomware, and has the application characteristics of “easy to deploy without center, less upgrade without network”, so it can be well combined with anti-virus systems, especially the whitelisting control mechanism, to provide support for users to cope with more complex security threats.
2. Work with us using the SDK we provide
Cubic-Crystal®™ Ransomware Monitoring and Blocking System is an information security product developed by Beijing Mike Technology Co., Ltd. for targeted prevention of encrypted ransomware.
It has the technical characteristics of encrypted ransomware identification without relying on fingerprint features, the intelligent processing capability of real-time discovery of malicious encryption behaviors and blocking, the strong ability to prevent unknown encrypted ransomware, and the advantages of application and deployment that do not require frequent upgrades over the Internet, which is an advantageous tool to deal with the threat of ransomware.
In order to better complement the advantages of various information security products and form an all-round, full-chain malware prevention and control capability, our company extracts the core functions of the ransomware monitoring and blocking system to form the SDK required for secondary development and application integration for use by our partners.
The SDK for integration is provided in the form of independent system services and device drivers, with basic ransomware identification and blocking capabilities, and can be called and set up using simple APIs, such as ransomware checking and killing, whitelist management, etc., or can be customized for functional development.
The integrated SDK demo program is an experiential version of the core functions of the ransomware monitoring and blocking system, and completes the basic monitoring, discovery, alarming and blocking functions of ransomware in the form of a sample application, so as to provide support for the combination of the core capabilities of the ransomware monitoring and blocking system and other multifaceted security capabilities that the partners themselves already have.
For example, partners can deeply integrate the ransomware discovery and blocking functions of the ransomware monitoring and blocking system with their own whitelisting mechanism to form more effective information security products with ransomware threat prevention capabilities.
Below is the main functional interface of the integration SDK demo program.
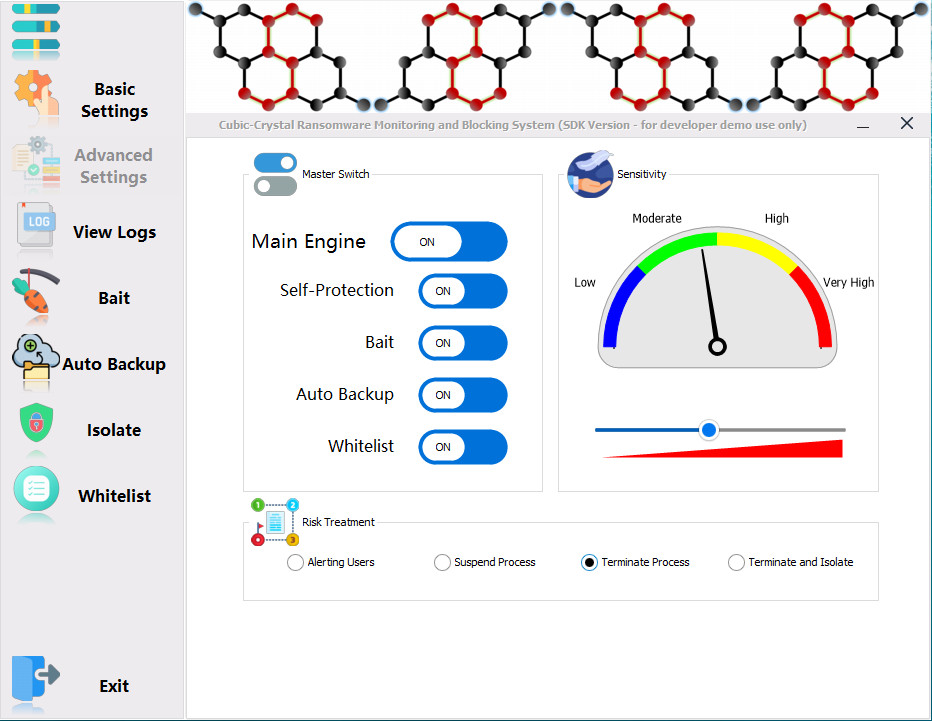
Main functional interface of the integration SDK
When ransomware is found, the system will check and kill ransomware-related processes by process ID or process group ID.
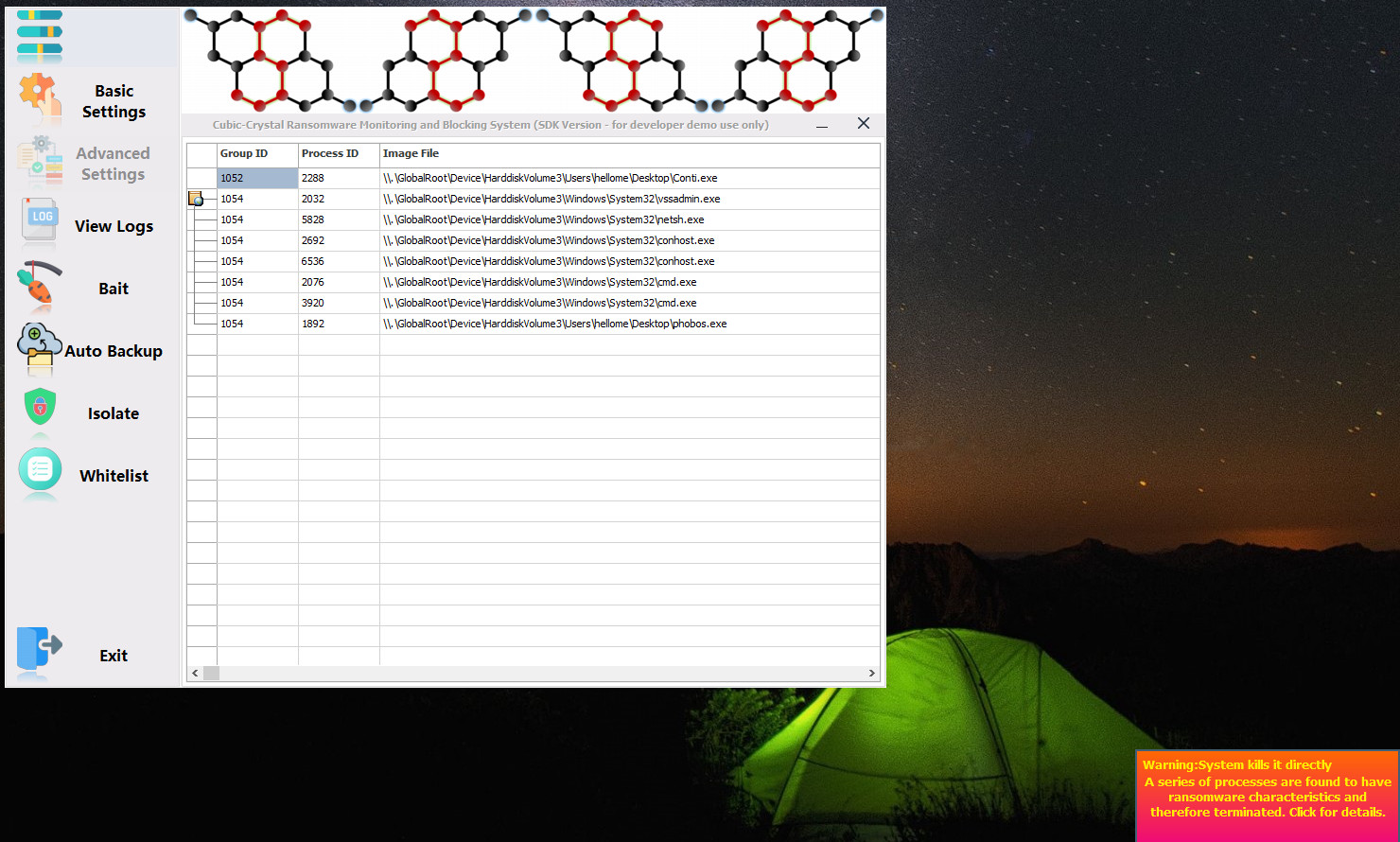
Kill ransomware and view logs
The user can define the location of the bait directory and specify what action triggers the trap when it occurs.
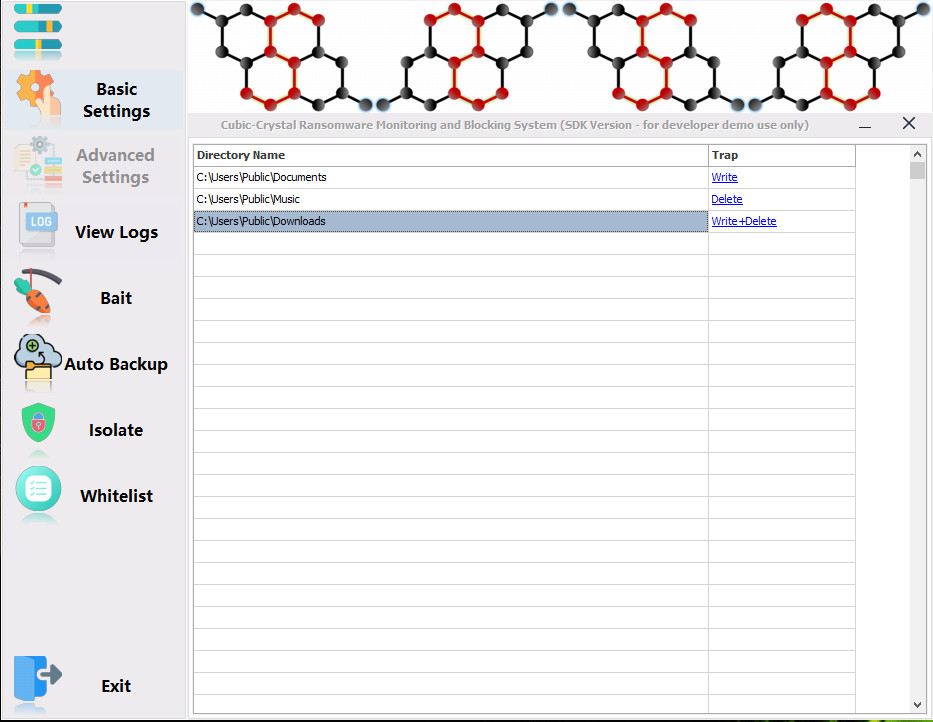
Define the location of the bait directory
In response to suspected ransomware processes, Cubic-Crystal®™ System recognizes the changes made to files and performs automatic backups at the user’s request.Users of the SDK can combine this capability with the backup mechanisms provided by cloud services to make the backup capability even more comprehensive.
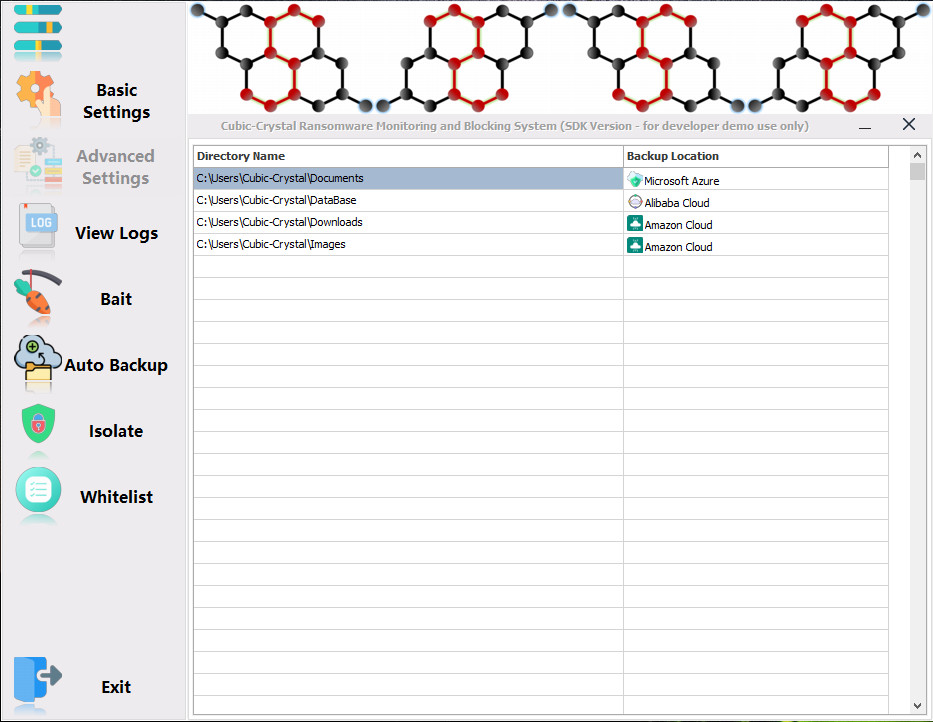
Combine automatic backup with cloud service backup
After the ransomware is found and killed, the system can encrypt its disk files and later store them safely in the quarantine.
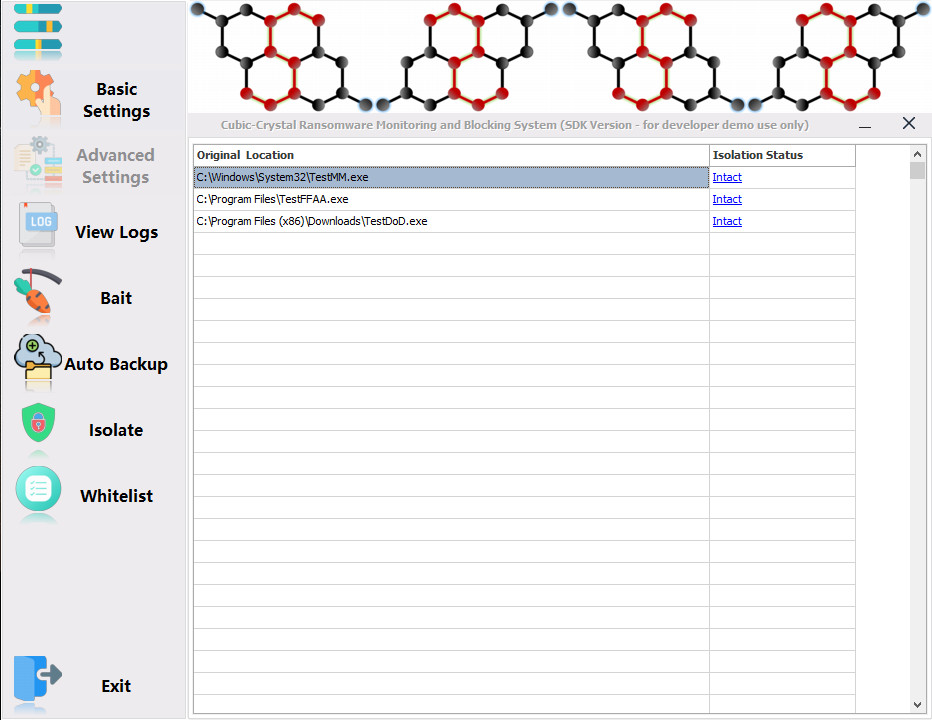
Isolate ransomwares safely
Cubic-Crystal®™ System discriminates ransomware based on behavioral characteristics, so even after very careful optimization, there is a low probability that some normal software will be recognized as ransomware. When this happens, simply add them to the whitelist manually. Rest assured that such cases are rare.
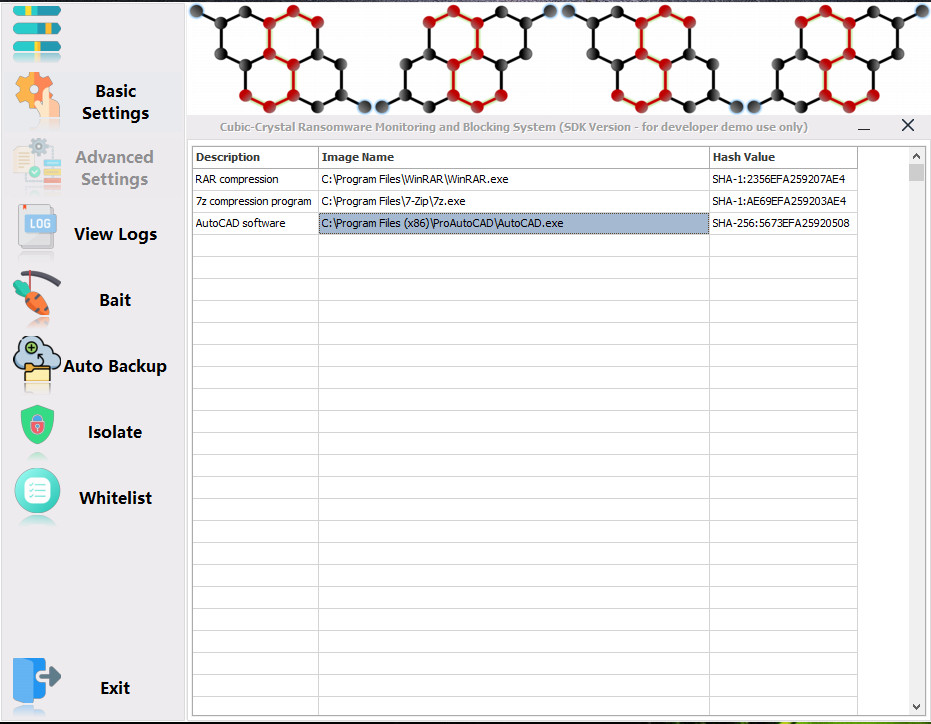
Very few normal software added to the whitelist
The Cubic-Crystal®™ Ransomware Monitoring and Blocking System, and the supporting integrated SDK for partners, is a new, effective, feasible and reliable solution to the increasingly rampant and extremely harmful ransomware threats, with profound technical accumulation and leading technical advantages.
It can solve the practical problems of fast encryption, strong destructiveness, high impact and high recovery cost of ransomware at minimal cost, and has the following features of being effective against unknown threats, able to stop the loss in time when ransom behavior occurs, and deployed off-network.
By cooperating with the majority of information security vendors and complementing their strengths and weaknesses, we will be able to provide strong support for the effective prevention of ransomware, and contribute to the data security and application security protection of end users.
Remember our slogan: Fighting ransomware with cryptography!