The growing threat of ransomware
By Beijing Mike
Ransomware is a type of malware that has historically been designed to encrypt data and make systems that rely on it unusable. Malicious actors then demand ransom in exchange for decrypting the data. Since 2019, we saw a huge rise in the number of ransomware attacks, where many companies were faced with their IT infrastructure and data becoming encrypted and many got their data stolen by different ransomware groups.
So many organizations worldwide have faced ransomware attacks, and looking at the statistics, the number of large organizations that have been impacted only seems to be rising. But has ransomware evolved over the last few years?
Ransomware is mostly used by attackers to exploit the weakest points in your infrastructure and then encrypt your data and infrastructure using some form of encryption method. Once the encryption is done, they leave a ransom note and wait. The only way to get access to the original data (or to be able to decrypt it) is by buying a decryption tool from the attackers using one of the digital currencies.
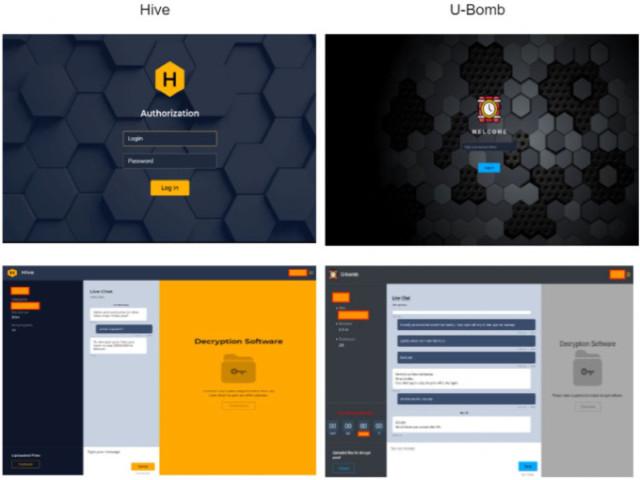
Hive (left) and U-Bomb (right) ransom chat portals
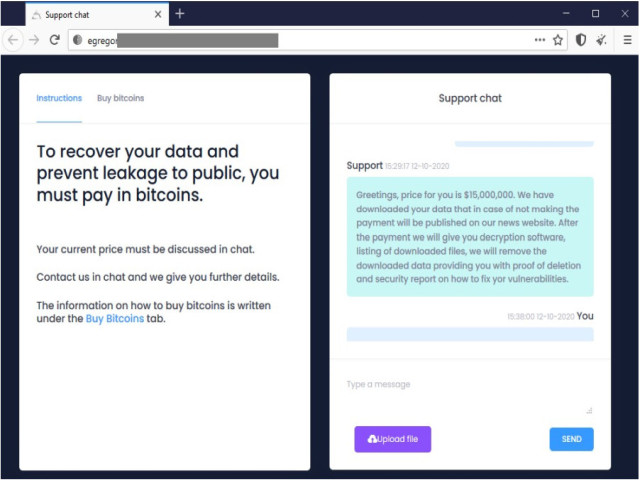
Ransomware operator chat support
The evolution of ransomware can be visualized in the following illustration.
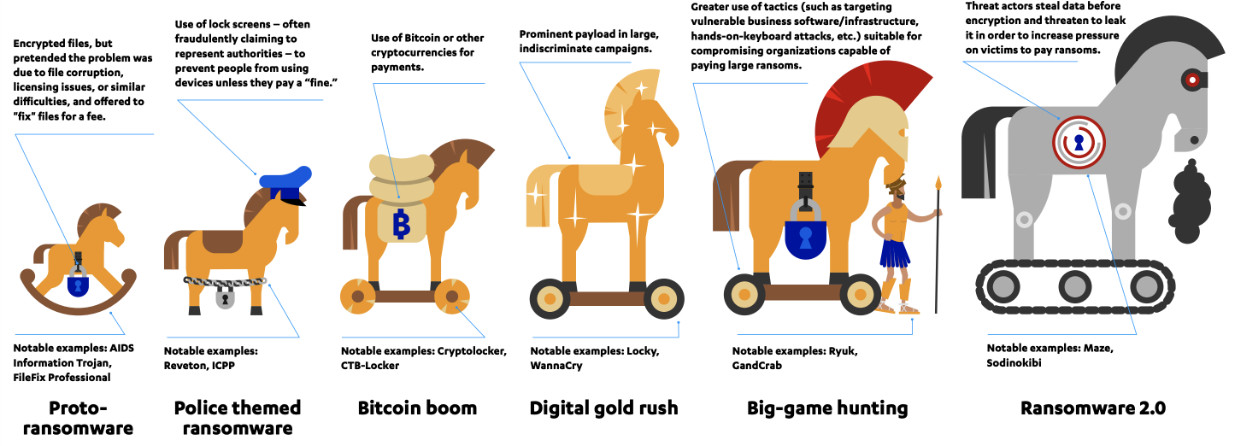
Evolution of ransomware
Let’s describe its evolution in a more refined way below.
The first known ransomware attack occurred in 1989, when a biologist named Joseph Popp sent infected floppy disks to attendees of the World Health Organization’s international AIDS conference. The disks contained a program that encrypted the victim’s files and demanded a ransom of $189 in return for the decryption key. Ransomware has evolved significantly over the years, becoming one of the most prominent and damaging types of cyberthreats.
Early history:
An early iteration of ransomware known as “screen lockers” falsely claimed to encrypt files. A significant turning point came with the emergence of the Gameover Zeus botnet, which began deploying a ransomware variant named CryptoLocker to target systems that were not profitable through wire/ACH fraud. This marked a significant shift in the evolution of ransomware as it moved from mere screen-locking tactics to genuine encryption-based attacks.
Ransomware worms:
Ransomware started using worm-like capabilities to spread rapidly in networks and across connected systems. This allowed it to propagate autonomously, infecting multiple devices and systems without requiring direct user interaction. Notorious worms like NotPetya and WannaCry have demonstrated the potential for widespread damage and financial losses.
Ransomware negotiation and payment process:
To facilitate ransom negotiations and payment, cybercriminals have established professional customer support systems. They often provide decryption tools or unlock codes upon receiving payment. Use of cryptocurrency in payment has made it easier for criminals to maintain their anonymity.
Advanced encryption and evasion techniques:
As cybersecurity measures improved, ransomware developers began employing more sophisticated encryption algorithms and techniques to evade detection. This included the use of asymmetric encryption, where separate keys are used for encryption and decryption, making it more challenging to crack the encryption without the private key.
Targeted ransomware:
Instead of indiscriminate attacks, cybercriminals started targeting specific organizations, particularly those that controlled valuable data or critical infrastructure. Threat actors conduct extensive reconnaissance to identify vulnerabilities and design tailored attacks.
Ransomware as a service (RaaS):
Ransomware evolved into a lucrative business model with the rise of RaaS platforms, which allow cybercriminals to purchase or lease ransomware variants and infrastructure from developers, streamlining the distribution process. This led to a significant increase in the number of attacks as more individuals with limited technical skill could carry out ransomware campaigns.
Targeting critical infrastructure:
Recent years have seen an alarming increase in ransomware attacks targeting critical infrastructure, including healthcare systems, government agencies, and utilities. These attacks have the potential to cause severe disruptions, endanger lives, and result in substantial economic damage. The Colonial Pipeline attack in 2021 is a notable example.
Supply chain attacks:
The REvil ransomware incident was a notable supply chain attack in which thousands of downstream customers were compromised through a vulnerability in Kaseya. Attackers focus on exploiting the weakest link in the chain, leveraging their access to data or systems. Some attacks are opportunistic, executed swiftly and targeting valuable assets, as seen with Lapsu$. In other instances, these attacks can evolve into sophisticated, multi-stage ransomware campaigns that may impact the primary target as well as its partners and customers.
Ransomware attacks increased by over 37% in 2023 (tracked between April 2022 and April 2023) compared to the previous year1 2, with the average enterprise ransom payment exceeding $100,0003, with a $5.3 million average demand4.
The proliferation of ransomware continues to pose a significant threat to organizations, individuals, and critical infrastructure worldwide. Cybercriminals constantly adapt and refine their tactics, leveraging leaked source code, advanced encryption schemes, and emerging programming languages to maximize their illicit gains.
Ransomware is always evolving as cybercriminals continuously adapt and refine their tactics and techniques. To protect against this ever-changing threat, it is crucial for individuals, organizations, and governments to remain vigilant and implement the latest, most robust cybersecurity measures.
However, the speed of ransomware updates and iterations is so fast, the number of variants is so large, and the forms of attack are so numerous that it is impossible to prevent it from compromising users’ networks and applications through traditional virus protection systems.
Titaniam’s State of Data Exfiltration & Extortion Report for 2022 finds that with attackers winning over 60% of the time5.
-
Over 70% of organizations surveyed were attacked within the last 5 years.
-
68% of those attacked had their data exfiltrated, and of those, 60% were subsequently extorted. Exfiltration rates are up 106% relative to 5 yrs ago.
-
While over 75% of surveyed organizations had all three major categories of ransomware protection in place i.e. prevention/detection, backup/ recovery, as well as traditional data protection, the majority of those attacked, 60%, were forced to give in to ransom demands.
-
Over 99% of study participants are looking for better data protection tools to overcome ransomware and extortion.
This proves that traditional data security tools are completely inadequate to manage the risk and impact of these attacks.
Cubic-Crystal®™ Ransomware Monitoring and Blocking System is a defense system for encryption type ransomware. Unlike conventional static defense products based on feature codes, it takes rich and comprehensive system-level behavioral monitoring as the engineering basis and accurate judgment of encryption operations as the theoretical support, realizes real-time monitoring and discovery of encryption-type ransomware, and possesses the linkage-based protection ability to block encryption ransomware behaviors in a timely manner when they occur.
It can provide users with effective anti-ransomware capabilities and has strong prevention and control capabilities against unknown encryption ransomware.It can help organizations strengthen their defenses, anticipate potential ransomware attacks, and respond effectively to mitigate their impact.
Here, let’s take a look at this revolutionary anti-ransomware product.
Remember our slogan: Fighting ransomware with cryptography!
-
Verizon Data Breach Report 2022: average ransomware payment $170,404 in 2022 ↩︎
-
McAfee Labs 2022 Threat Report: average ransomware payment was $112,446 in 2022 ↩︎
-
IBM X-Force Threat Intelligence Index 2022: average ransomware payment was $312,493 in 2022 ↩︎
-
Coveware Ransomware Report 2022: average ransomware demand for enterprises was $5.3 million in 2022 ↩︎
-
Titaniam Ransomware Research Report: State of Data Exfiltration and Extortion 2022 ↩︎