Introduction of Cubic-Crystal System
By Beijing Mike
1. Introduction
Cubic-Crystal®™ Ransomware Monitoring and Blocking System is a defense system for encryption type ransomware. Unlike conventional static defense products based on feature codes, it features rich and comprehensive system-level behavioral monitoring as the engineering basis and accurate judgment of encryption operations as the theoretical support, realizes real-time monitoring and discovery of encryption-type ransomware, and possesses the linkage-based protection ability to block encryption ransomware behaviors in a timely manner when they occur. It can provide users with effective anti-ransomware capabilities and help prevent and control unknown encryption ransomware.
2. Features
As an all-round, multi-level encryption ransomware defense system, it is capable of implementing three-level defense against ransomware encryption behavior before, during and after the event, which can be used as an effective supplement to the terminal security protection system so as to form a comprehensive, holistic ransomware intrusion prevention and blocking system.
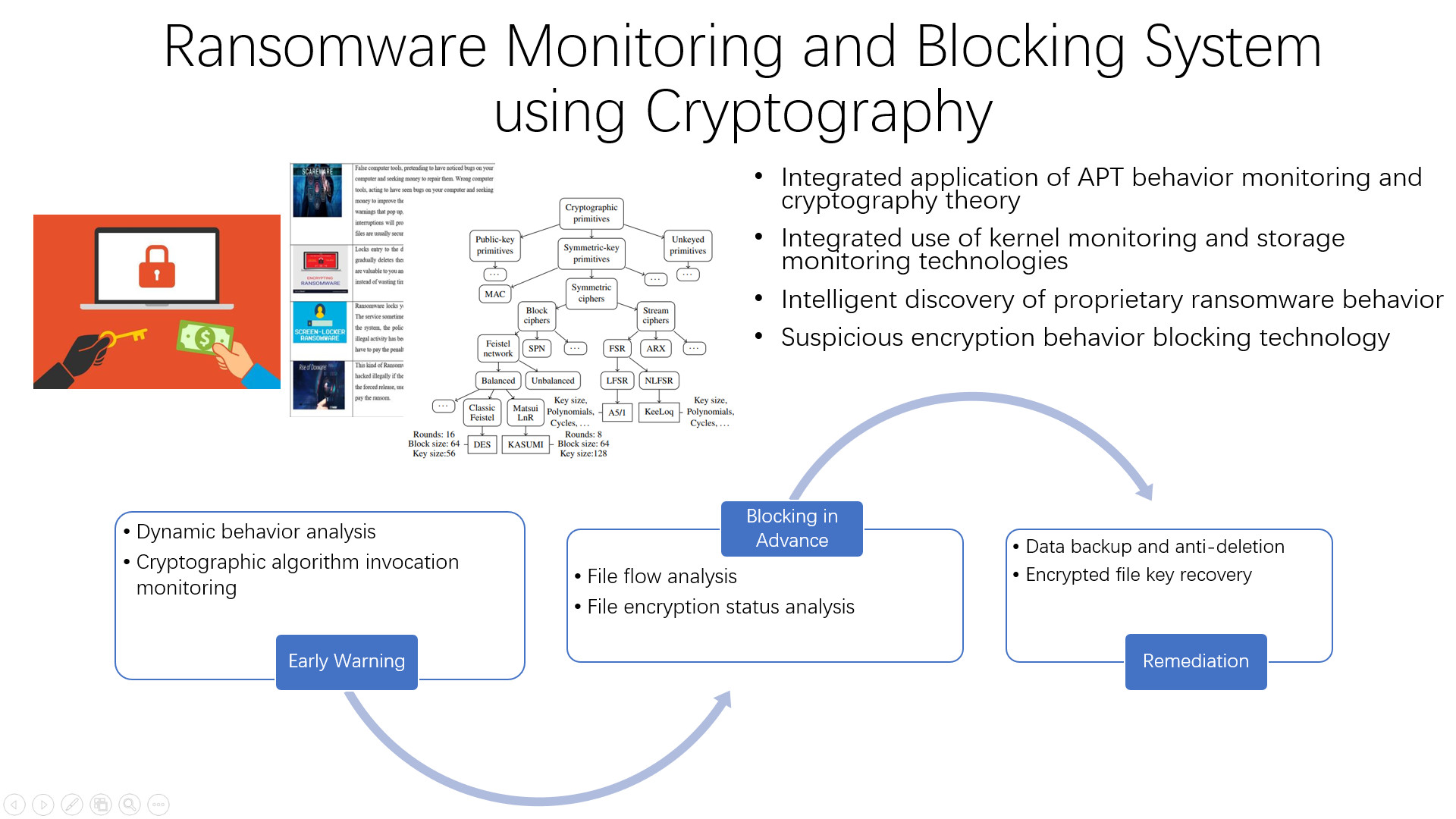
Multi-level Preventive Mechanism
The system has the following technical features:
-
Integrated application of APT behavior monitoring and cryptography theory
-
Combined use of process monitoring and storage monitoring techniques
-
Proprietary ransomware behavior intelligent discovery technology
-
Proprietary suspicious encryption behavior discovery and blocking technology
-
Ability to prevent unknown encryption ransomware
3. System Compositions and Hierarchies
The system function consists of 7 core modules:
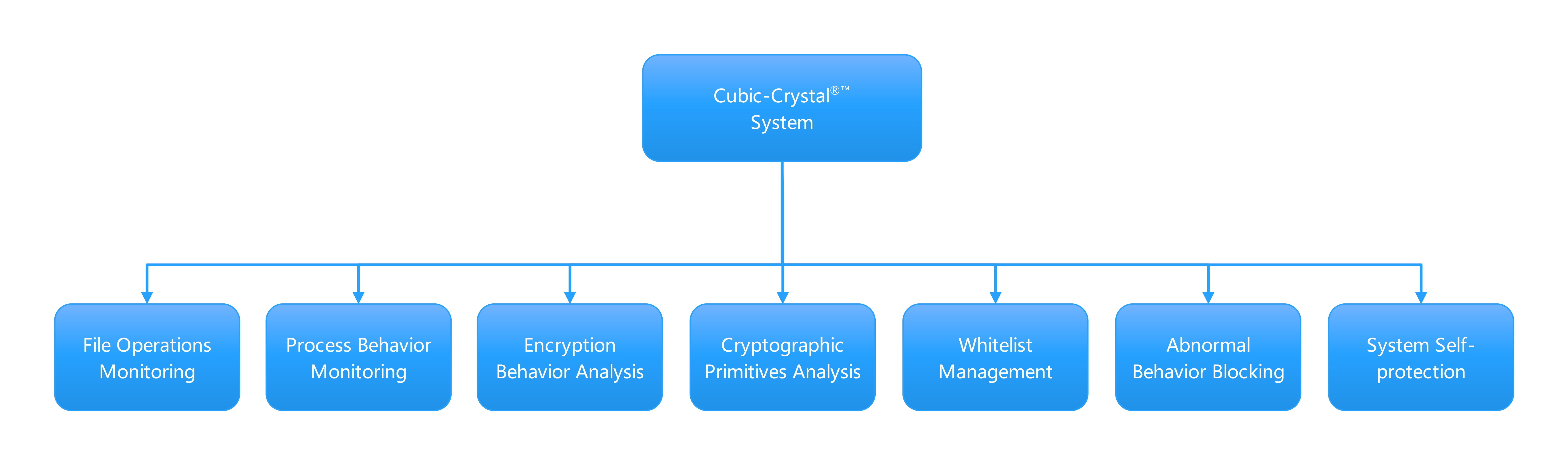
System Components
The system is designed to be divided into 4 levels, including 17 aspects of the core correlation operation, in order to implement a comprehensive linkage of ransomware encryption behavior monitoring, prevention and blocking.
Among them:
-
All operations in each horizontal layer are linked and interact with each other;
-
The operations of the upper layer are supported by the concretization of those of the lower layer;
-
The kernel filtering layer is divided into 3 specific filtering control procedures (distinguished by color) for files, processes and passwords, that also belong to the associated operations, providing support for the corresponding operations in the upper layer (the upper and lower correspondences shown in the diagram) and linking through the communication between the associated operations in the upper layer.
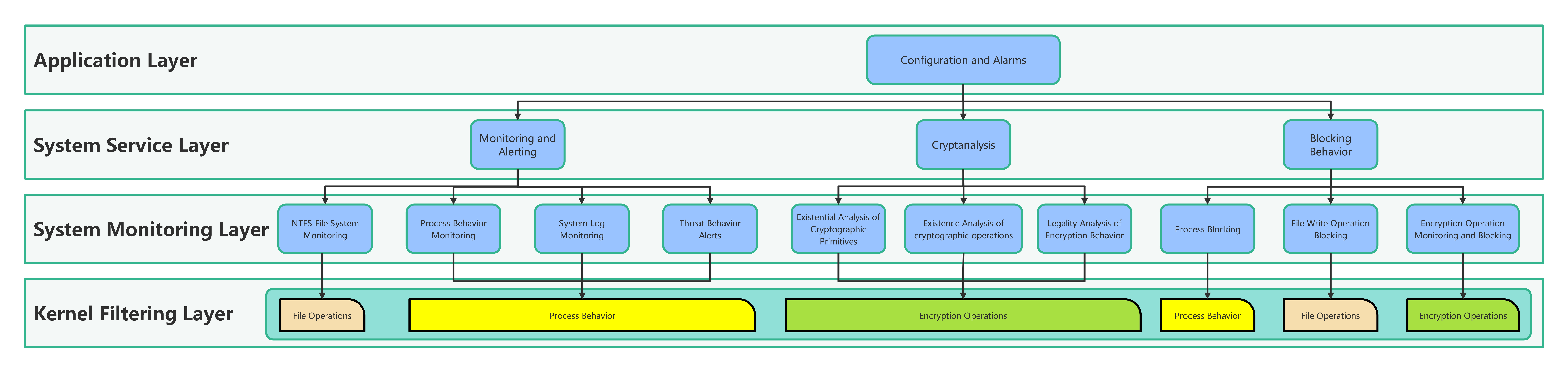
System Hierarchies
4. System Function Points:
-
Real-time monitoring of all sensitive file operations of concern, including reading, writing, deleting and renaming;
-
Dynamically analyze whether files are encrypted and by whom (which process);
-
Dynamically analyze whether processes have encryption operation primitives;
-
Dynamically analyze and determine whether the encryption operation of a process is reasonable, using an updatable policy;
-
Filter key processes at the user setting level according to the whitelist mechanism;
-
Timely alarm and block suspicious behaviors;
-
Support user-specified directory high-level priority protection;
-
Support ransomware behavior trapping;
-
Support ransomware behavior blocking in the form of no files;
-
Support ransomware blocking in the form of PowerShell scripts;
-
Support monitoring and blocking the behavior of unknown encryption ransomware.
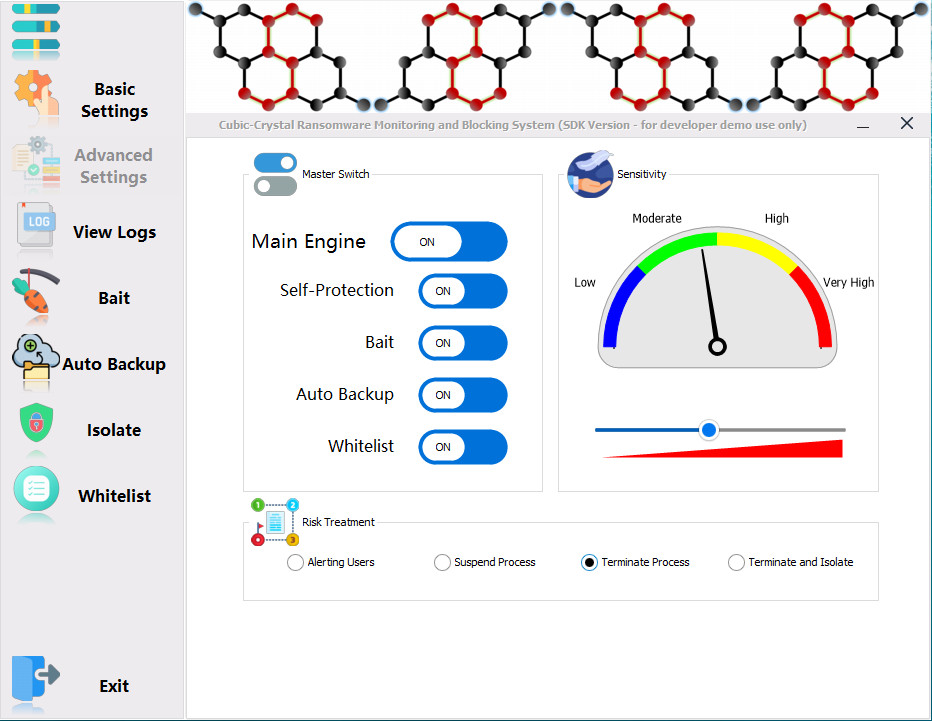
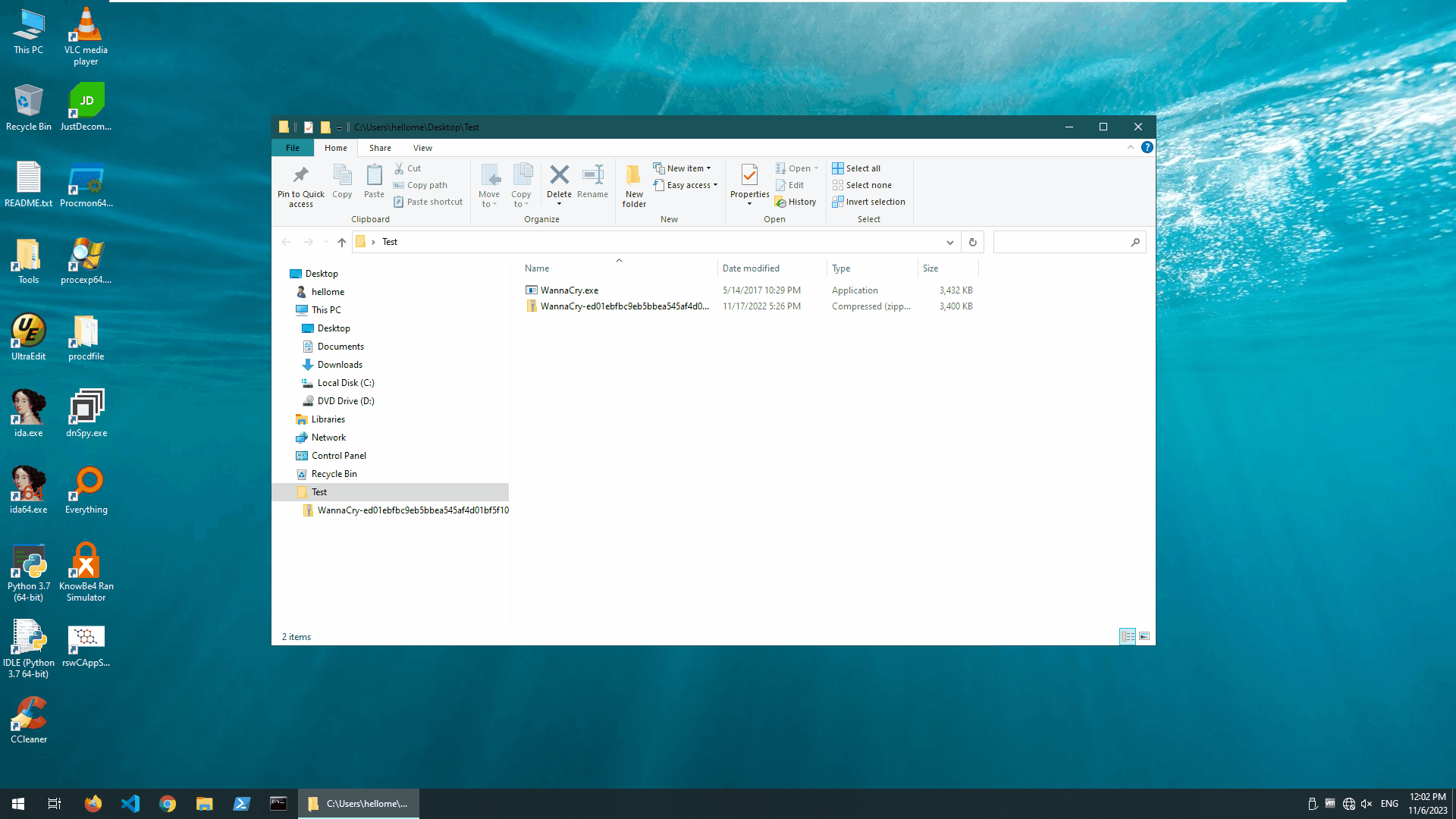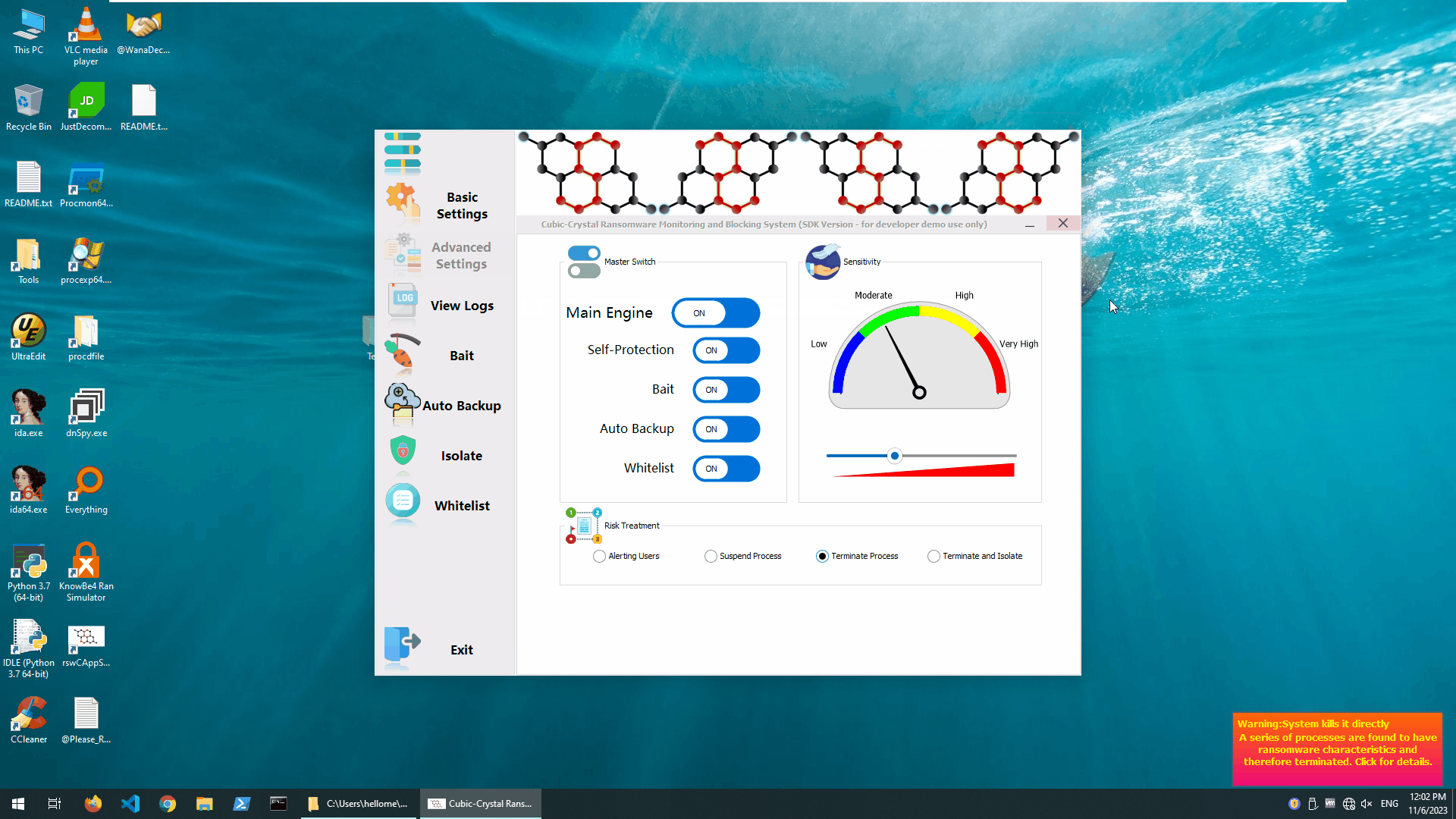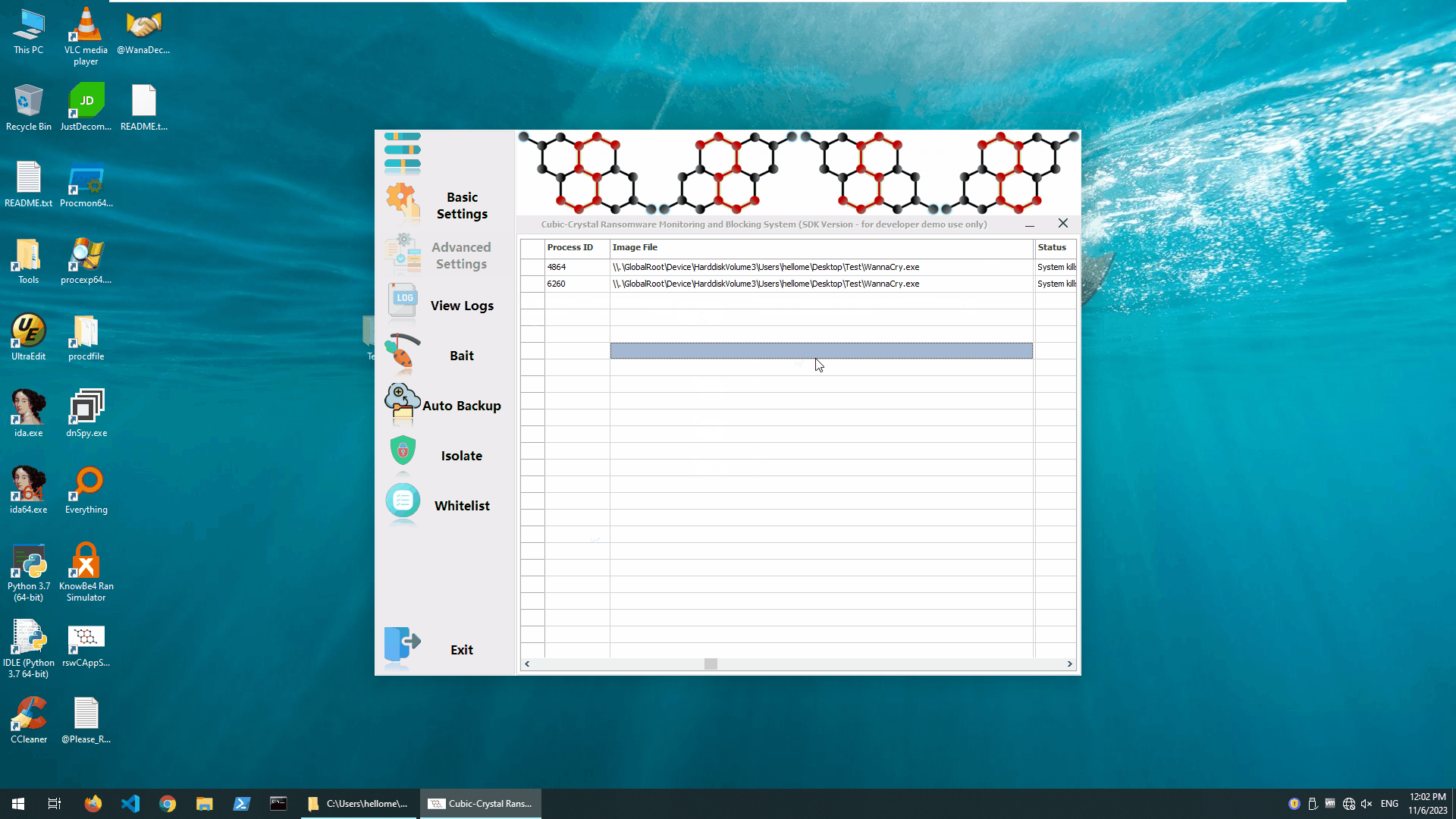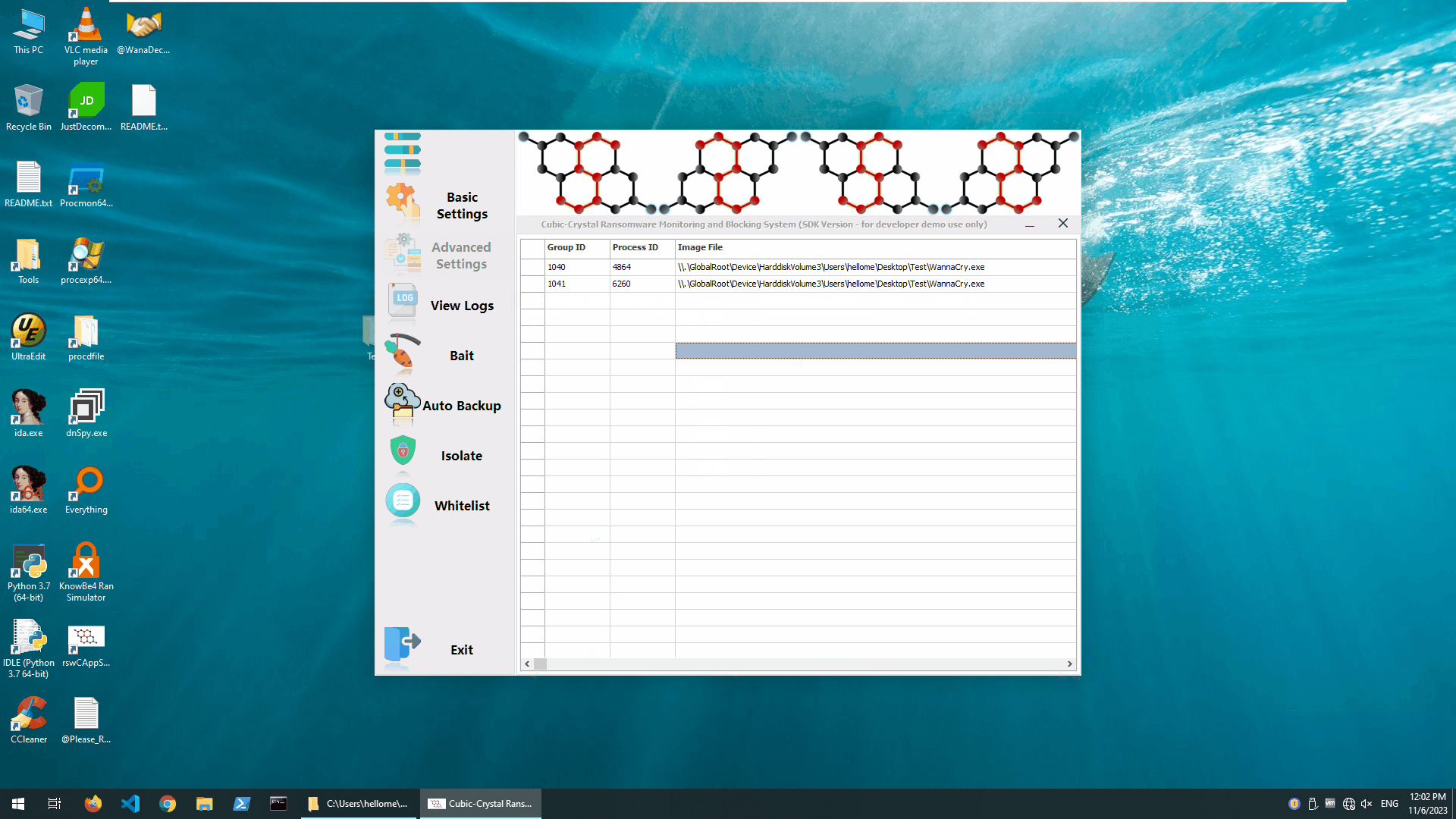
The main screen of the application (SDK Version)
5. Advantageous Technology
- Fast File Indexing and Monitoring Technology
It is able to access and operate all kinds of files by going deep into the bottom layer of the file system, and realize efficient and fast file indexing and monitoring with low system resource consumption.
- File stream and encryption state analysis technology
Scanning sensitive file stream operations of concern, through in-depth analysis of file operation correlation and file content change characteristics, it can detect abnormal encryption operations on files in near real-time, capture encryption process status for correlation analysis, and alarm and block according to the user’s predefined configurations.
- Process encryption operation primitive discovery technology
Based on specific graph theory algorithms, it can discover whether a process is capable of encryption by comprehensively analyzing the logical characteristics of encryption primitives and encryption parameters. Unrestricted by specific cryptographic algorithm logic and cryptographic algorithm implementation, it can discover whether there is a dedicated or special type of cryptographic logic, and has a good ability to pre-discover unknown cryptographic algorithm encryption behavior.
- Proprietary ransomware behavior monitoring technology
In response to the latest technological development of ransomware, we have summarized the behavioral characteristics of fileless/scripted ransomware and implemented targeted monitoring and defense blocking, which is capable of resisting and effectively blocking newer and even unknown ransomware families.
6. How it works
Below we demonstrate how the system works with a practical example.
First, let’s illustrate our basic demo environment. The environment is running Windows 10 operating system, the disk space is about 80GB, the space occupied by the installed space is about 45GB. among them, the size of the document used for testing is about 500MB, the size of the picture used for testing is about 400MB, and the audio and video files used for testing are about 1.7GB. the size of the space of the operating system program is about 11GB, and the space of the program of the tool used for your own installation is About 3GB.

basic demo environment
The ransomware we used for the demo was WannaCry, for it was a classic, landmark and iconic ransomware.
We “detonated” the WannaCry ransomware in our test environment with no protection turned on. The SHA256 value of this ransomware sample is ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.
The ransomware sample completed its damage to the test environment in about 1 minute and 30 seconds, popping up the classic ransom payment prompt window.

Wannacry encrypted unprotected system
As you can see, the ransomware sample encrypted about 25,000 files in a very short period of time. And it’s worth noting that WannaCry’s encryption speed is still relatively slow compared to popular ransomware today.
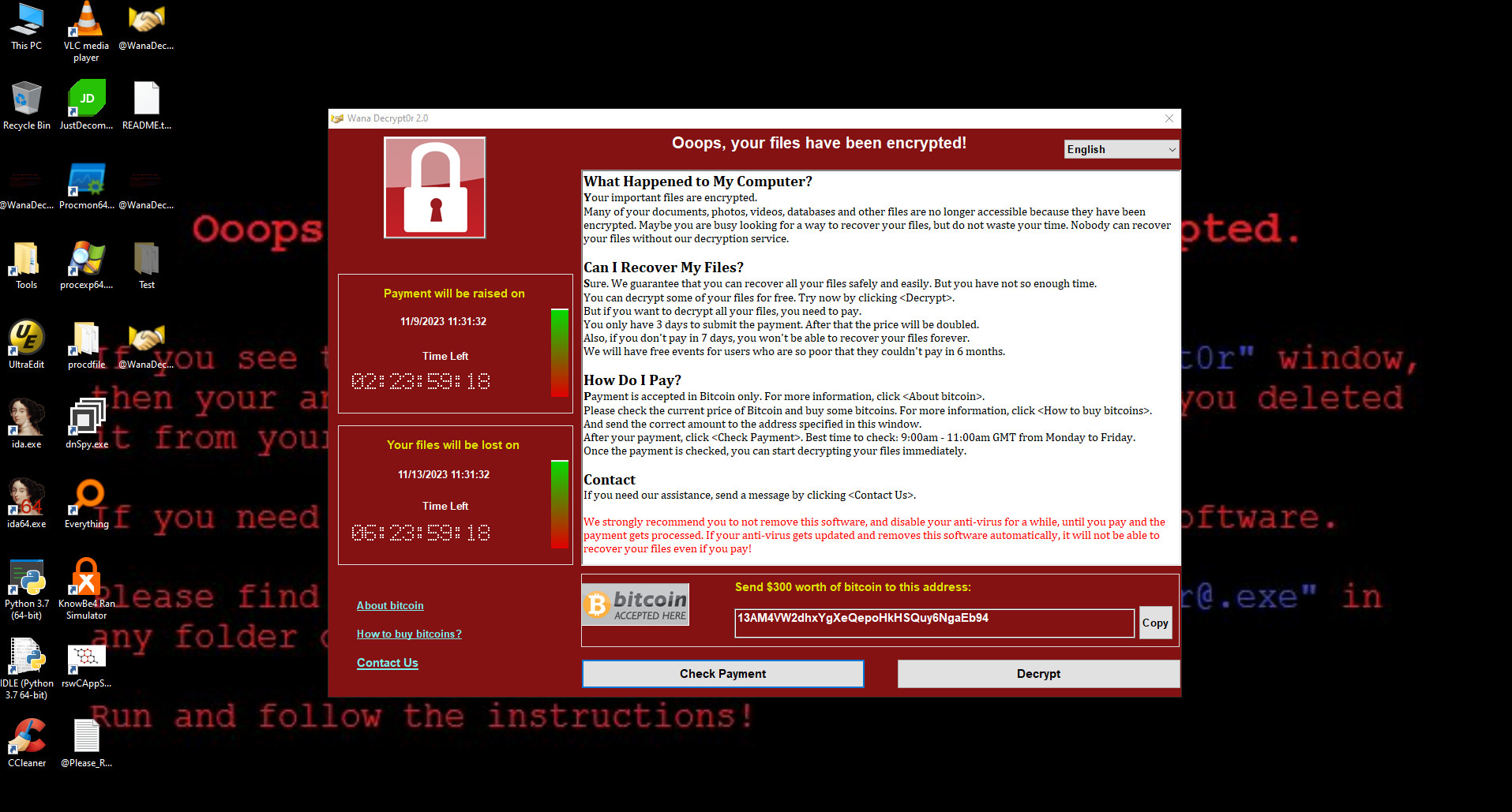
Wannacry ransomware alert window
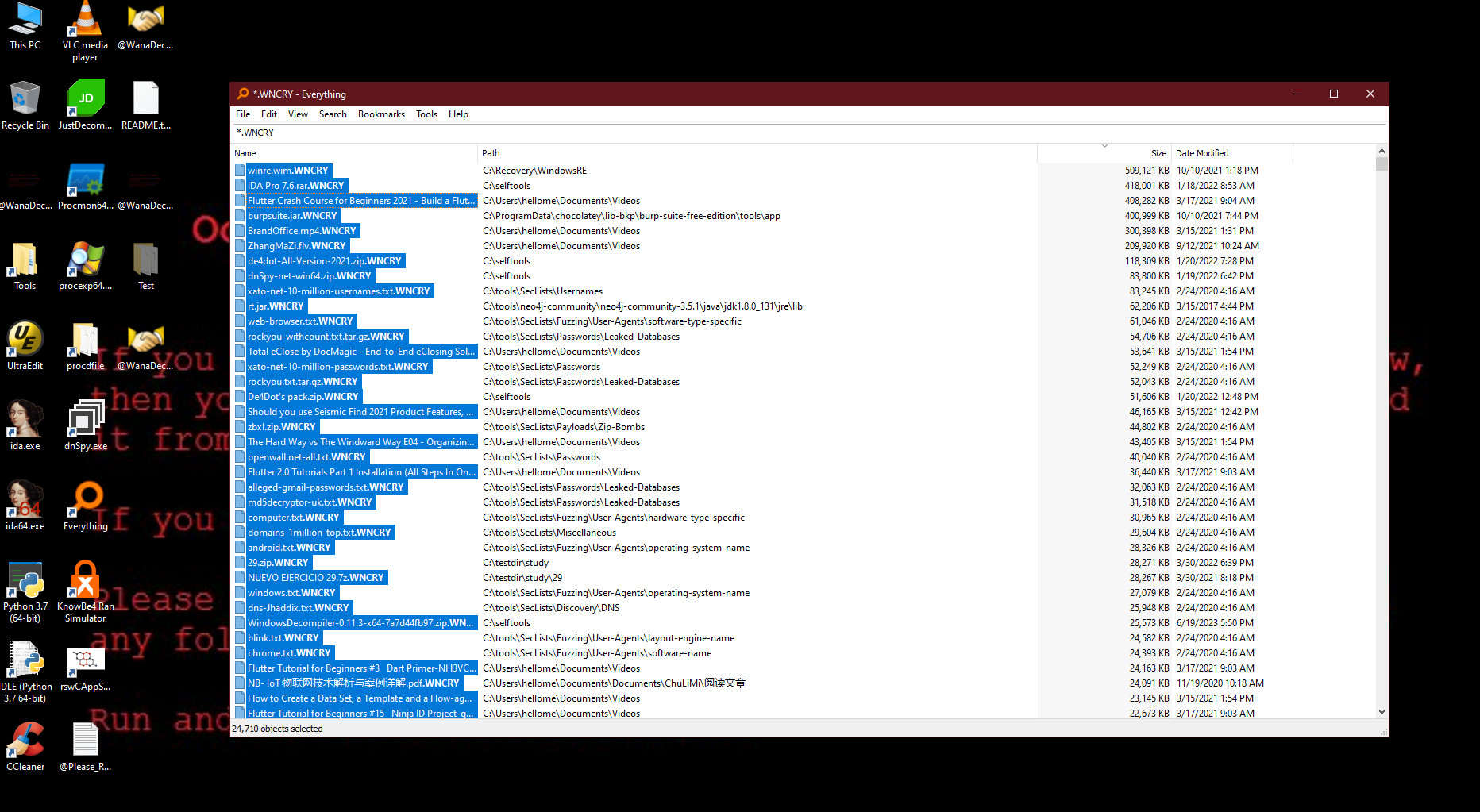
Wannacry encrypted a lot of files
Let’s take a look at how the Cubic-Crystal®™ System stops WannaCry ransomware.
It’s very simple: we just flipped the switch on the main engine and it only took a few milliseconds for the Cubic-Crystal®™ System to determine that it was a crypto-type ransomware and block it.In this test, we “detonated” the Wannary ransomware 2 times.
Blocking Wannacry Ransomware
Let’s check how many files we have lost in order to determine that this is a ransomware.
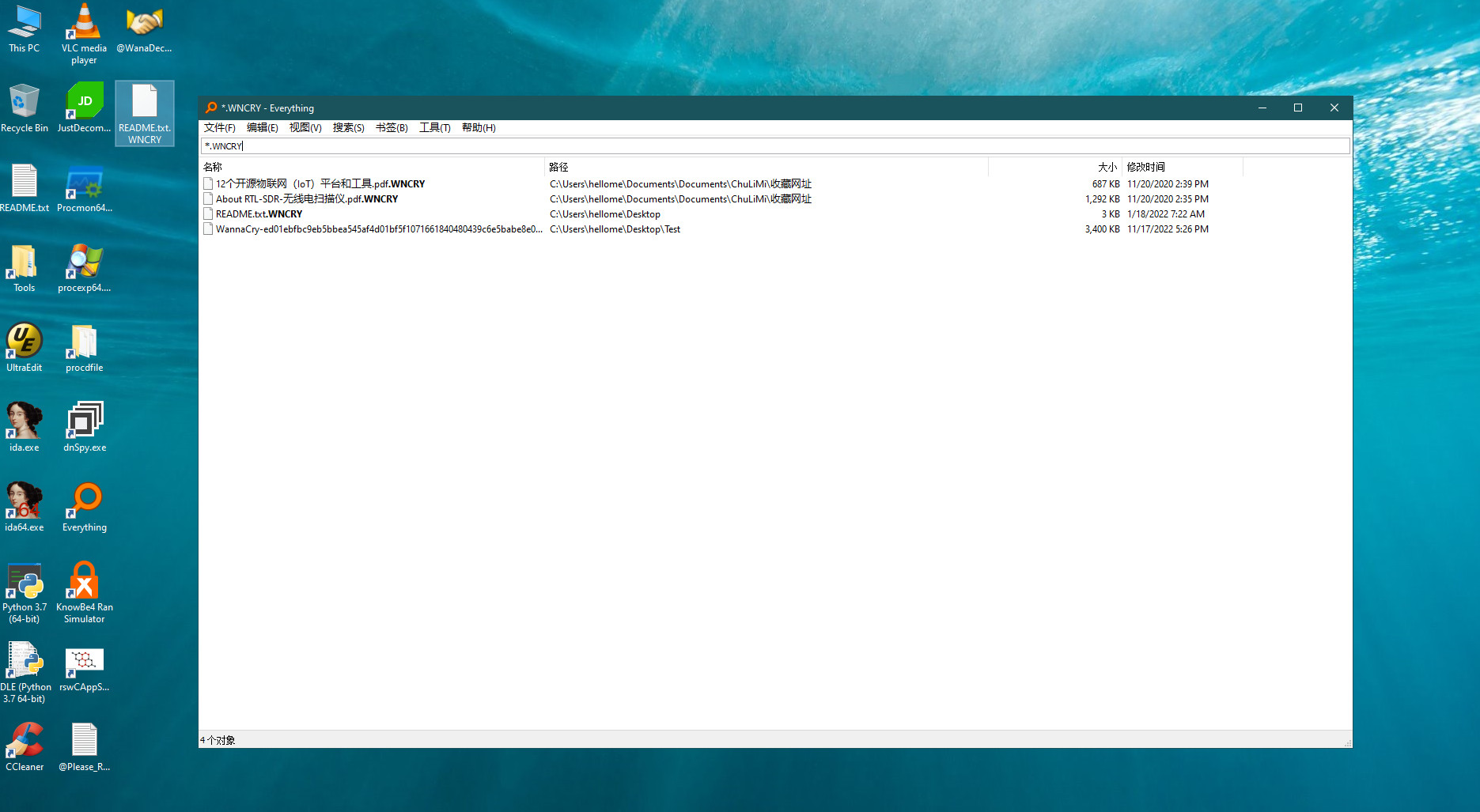
We lost 4 files
Yes, we lose files to determine if a process or group of processes is malicious ransomware. Remember, Cubic-Crystal®™ System is not based on file checksums or signature codes but a behavior-based ransomware monitoring and blocking system. Because of this technical feature, it has the ability to protect ourselves against unknown ransomware.
Using Cubic-Crystal®™ System is so easy!
Remember our slogan: Fighting ransomware with cryptography!